Introduction
OpenVMM is a modular, cross-platform Virtual Machine Monitor (VMM), written in Rust.
Although it can function as a traditional VMM, OpenVMM's development is currently focused on its role in the OpenHCL paravisor.
The project is open-source, MIT Licensed, and developed publicly at microsoft/openvmm on GitHub.
Cross-Platform
OpenVMM supports a variety of host operating systems, architectures, and virtualization backends:
| Host OS | Architecture | Virtualization API |
|---|---|---|
| Linux (paravisor) | x64 / Aarch64 | MSHV (using VSM / TDX / SEV-SNP) |
| Windows | x64 / Aarch64 | WHP (Windows Hypervisor Platform) |
| Linux | x64 / Aarch64 | KVM |
| x64 | MSHV (Microsoft Hypervisor) | |
| macOS | Aarch64 | Hypervisor.framework |
Running in the OpenHCL paravisor
OpenVMM is the VMM that runs in the OpenHCL paravisor.
Unlike in traditional virtualization, where a VMM runs in a privileged host/root partition and provides virtualization services to a unprivileged guest partition, the "paravisor" model enables a VMM to provide virtualization services from within the guest partition itself.
It can be considered a form of "virtual firmware", running at a higher privilege level than the primary guest OS.
Paravisors are quite exciting, as they enable a wide variety of useful and novel virtualization scenarios! For example: at Microsoft, OpenHCL plays a key role in enabling several important Azure scenarios:
-
Enabling existing workloads to seamlessly leverage Azure Boost (Azure's next-generation hardware accelerator), without requiring any modifications to the guest VM image.
-
Enabling existing guest operating systems to run inside Confidential VMs.
-
Powering Trusted Launch VMs - VMs that support Secure Boot, and include a vTPM.
Standalone VMM
OpenVMM can also run as a general-purpose VMM on a Windows, Linux, or macOS host. At the moment, this is primarily a development vehicle: most of the same code runs in OpenVMM on a host and OpenVMM in a paravisor, and it is often easier to test it on a host.
We will continue to build and test OpenVMM in this configuration, but currently we are not focused on the goal of supporting this for production workloads. It is missing many of the features and interface stability that are required for general-purpose use. We recommend you consider other Rust-based VMMs such as Cloud Hypervisor for such use cases.
Relationship to other Rust-based VMMs
OpenVMM's core security principles are aligned with those of the Rust-based Cloud Hypervisor, Firecracker, and crosvm projects, which is why we also chose to write OpenVMM in Rust. However, OpenVMM's unique goal of running efficiently in a paravisor environment made it difficult to leverage existing projects. OpenVMM requires fine-grained control over thread and task scheduling in order to avoid introducing jitter and other performance issues into guest VMs. It is difficult to achieve these requirements with traditional, thread-based designs.
Instead, OpenVMM uses Rust's async support throughout its codebase, decoupling
the policy details of where code runs (which OS threads) from the mechanism of
what runs (device-specific emulators). In a paravisor or resource-constrained
environment, OpenVMM can run with one thread per guest CPU and ensure that
device work is cooperatively scheduled along with the guest OS. In more
traditional virtualization host, OpenVMM can run with one thread per device to
use host CPUs to fully parallelize guest CPU and IO processing.
This approach has a significant impact on the design and implementation of the codebase, and bringing this model to an existing VMM would be a major undertaking. We came to the conclusion that a new project was the best way to achieve this goal.
We are indebted to the Rust VMM community for their trailblazing work. Now that the OpenVMM project is open source, we hope to find ways to collaborate on shared code while maintaining the benefits of the OpenVMM architecture.
Guest Compatibility
Similar to other general-purpose VMMs (such as Hyper-V, QEMU, VirtualBox), OpenVMM is able to host a wide variety of both modern and legacy guest operating systems on-top of its flexible virtual hardware platform.
-
Modern operating systems can boot via UEFI, and interface with a wide selection of paravirtualized devices for services like networking, storage, and graphics.
-
Legacy x86 operating systems can boot via BIOS, and are presented with a PC-compatible emulated device platform which includes legacy hardware such as IDE hard-disk/optical drives, floppy disk drives, and VGA graphics cards.
OpenVMM is regularly tested to ensure compatibility with popular operating systems (such as Windows, Linux, and FreeBSD), and strives to maintain reasonable compatibility with other, more niche/legacy operating systems as well.
To learn more about different facets of the OpenVMM project, check out the following links:
| Getting Started: OpenVMM | Running OpenVMM as traditional host VMM |
| Getting Started: OpenHCL | Running OpenVMM as a paravisor (OpenHCL) |
| Developer Guide: Getting Started | Building OpenVMM / OpenHCL locally |
| [Github] microsoft/openvmm | Viewing / Downloading OpenVMM source code |
| [Github] OpenVMM issue tracker | Reporting OpenVMM issues |
OpenVMM
OpenVMM can be configured to run as a conventional hosted, or "type-2" Virtual Machine Monitor (VMM).
At the moment, OpenVMM can be built and run on the following host platforms:
| Host OS | Architecture | Virtualization API |
|---|---|---|
| Windows | x64 / Aarch64 | WHP (Windows Hypervisor Platform) |
| Linux | x64 | KVM |
| x64 | MSHV (Microsoft Hypervisor) | |
| macOS | Aarch64 | Hypervisor.framework |
When compiled, OpenVMM consists of a single standalone openvmm / openvmm.exe
executable.1
As you explore the OpenVMM repo, you may find references to the term HvLite.
HvLite was the former codename for OpenVMM, so whenever you see the term "HvLite", you can treat it as synonymous to "OpenVMM".
We are actively migrating existing code and docs away from using the term "HvLite".
Notable Features
This non-exhaustive list provides a broad overview of some notable features, devices, and scenarios OpenVMM currently supports.
- Boot modes
- UEFI - via
microsoft/mu_msvmfirmware - BIOS - via the Hyper-V PCAT BIOS firmware
- Linux Direct Boot
- UEFI - via
- Devices
- Paravirtualized
- Direct Assigned (experimental, WHP only)
- Emulated
- vTPM
- NVMe
- Serial UARTs (both 16550, and PL011)
- Legacy x86
- i440BX + PIIX4 chipset (PS/2 kbd/mouse, RTC, PIT, etc)
- IDE HDD/Optical, Floppy
- PCI
- VGA graphics (experimental)
- Device backends
- Graphics / Mouse / Keyboard (VNC)
- Serial (term, socket, tcp)
- Storage (raw img, VHD/VHDx, Linux blockdev, HTTP)
- Networking (various)
- Management APIs (unstable)
- CLI
- Interactive console
- gRPC
- ttrpc
For more information on any / all of these features, see their corresponding pages under the Reference section of the OpenVMM Guide.
...though, as you may be able to tell by looking at the sidebar, that section of the Guide is currently under construction, and not all items have corresponding pages at this time.
Before heading on to Running OpenVMM, please take a moment to read and understand the following important disclaimer:
In recent years, development efforts in the OpenVMM project have primarily focused on OpenHCL (AKA: OpenVMM as a paravisor).
As a result, not a lot of "polish" has gone into making the experience of running OpenVMM in traditional host contexts particularly "pleasant". This lack of polish manifests in several ways, including but not limited to:
- Unorganized and minimally documented management interfaces (e.g: CLI, ttrpc/grpc)
- Unoptimized device backend performance (e.g: for storage, networking, graphics)
- Unexpectedly missing device features (e.g: legacy IDE drive, PS/2 mouse features)
- No API or feature-set stability guarantees whatsoever.
At this time, OpenVMM on the host is not yet ready to run end-user workloads, and should should be treated more akin to a development platform for implementing new OpenVMM features, rather than a ready-to-deploy application.
though, depending on the platform and compiled-in feature-set, some additional DLLs and/or system libraries may need to be installed.
Running OpenVMM
This page offers a high-level overview of different ways to launch and interact with OpenVMM.
These examples are by no means "exhaustive", and should be treated as a useful jumping-off point for subsequent self-guided experimentation with OpenVMM.
Obtaining a copy of OpenVMM
To get started, ensure you have a copy of the OpenVMM executable and its runtime dependencies, via one of the following options:
Building OpenVMM Locally
Follow the instructions on: Building OpenVMM.
Pre-Built Binaries
If you would prefer to try OpenVMM without building it from scratch, you can download pre-built copies of the binary from OpenVMM CI.
Simply select a successful pipeline run (should have a Green checkbox), and
scroll down to select an appropriate *-openvmm artifact for your particular
architecture and operating system. You must be signed into GitHub in order
to download artifacts.
Examples
These examples all use cargo run --, with the assumption that you are a
developer building your own copy of OpenVMM locally!
To run these examples using a pre-compiled copy of OpenVMM, swap cargo run -- with /path/to/openvmm.
If you run into any issues, please refer to Troubleshooting.
Preface: Quitting OpenVMM
By default, OpenVMM will connect the guests's COM1 serial port to the current terminal session, forwarding all keystrokes directly to the VM.
As such, a simple ctrl-c does not suffice to quit OpenVMM!
Instead, you can type crtl-q to enter OpenVMM's interactive console, and enter q to quit.
Sample Linux Kernel, via direct-boot
This example will launch Linux via direct boot (i.e: without going through UEFI
or BIOS), and appends single to the kernel command line.
The Linux guest's console will be hooked up to COM1, and is relayed to the host terminal by default.
To launch Linux with an interactive console into the shell within initrd, simply run:
cargo run
This works by setting the default [env] vars in .cargo/config.toml to
configure OpenVMM to use a set of pre-compiled test kernel + initrd images,
which are downloaded as part of the cargo xflowey restore-packages command.
Note that this behavior only happens when run via cargo run (as cargo is the
tool which ensures the required env-vars are set).
The source for the sample kernel + initrd can be found on the microsoft/openvmm-deps repo.
The kernel and initrd can be controlled via options:
--kernel <PATH>: The kernel image. Must be an uncompressed kernel (vmlinux, not bzImage).--initrd <PATH>: The initial ramdisk image.-c <STRING>or--cmdline <STRING>: Extra kernel command line options, such asroot=/dev/sda.
Windows, via UEFI
This example will launch a modern copy of Windows via UEFI, using the mu_msvm
firmware package.
A copy of the mu_msvm UEFI firmware is automatically downloaded via cargo xflowey restore-packages.
cargo run -- --uefi --disk memdiff:path/to/windows.vhdx --gfx
For more info on --gfx, and how to actually interact with the VM using a
mouse/keyboard/video, see the Graphical Console
docs.
The file windows.vhdx can be any format of VHD(X).
Note that OpenVMM does not currently support using dynamic VHD/VHDX files on Linux hosts. Unless you have a fixed VHD1 image, you will need to convert the image to raw format, using the following command:
qemu-img convert -f vhdx -O raw windows.vhdx windows.img
Also, note the use of memdiff, which creates a memory-backed "differencing
disk" shim between the VMM and the backing disk image, which ensures that any
writes the VM makes to the VHD are not persisted between runs. This is very
useful when iterating on OpenVMM code, since booting the VM becomes repeatable
and you don't have to worry about shutting down properly. Use file instead for
normal persistent storage.
DOS, via PCAT BIOS
While DOS in particular is not a scenario that the OpenVMM has heavily invested in, the fact DOS is able to boot in OpenVMM serves as a testament to OpenVMM's solid support of legacy x86 devices and infrastructure.
The following command will boot a copy of DOS from a virtual floppy disk, using the Hyper-V PCAT BIOS.
Booting via PCAT is not just for DOS though! Many older operating systems, including older copies of Windows / Linux, require booting via BIOS.
cargo run -- --pcat --gfx --floppy memdiff:/path/to/msdos.vfd --pcat-boot-order=floppy,optical,hdd
OpenVMM Troubleshooting
This page includes a miscellaneous collection of troubleshooting tips for common issues you may encounter when running OpenVMM.
If you are still running into issues, consider filing an issue on the OpenVMM GitHub Issue tracker.
failed to open /dev/kvm/
Error:
fatal error: failed to launch vm worker
Caused by:
0: failed to launch worker
1: failed to create the prototype partition
2: kvm error
3: failed to open /dev/kvm
4: Permission denied (os error 13)
Solution:
When launching from a Linux/WSL host, your user account will need permission to
interact with /dev/kvm.
For example, you could add yourself to the group that owns that file:
sudo usermod -a -G <group> <username>
For this change to take effect, you may need to restart. If using WSL2, you can
simply restart WSL2 (run wsl --shutdown from Powershell and reopen the WSL
window).
Alternatively, for a quick-and-dirty solution that will only persist for the duration of the current user session:
sudo chown <username> /dev/kvm
Next Steps
To learn more about how OpenVMM works, and how to interact with it:
| Reference: OpenVMM Features | Configure and interact with OpenVMM |
| Dev Guide: Building OpenVMM | Build OpenVMM locally |
| Reference: OpenVMM Architecture | Understand how OpenVMM works "under the hood" |
OpenHCL
OpenHCL is an execution environment which runs OpenVMM as a paravisor.
Unlike in traditional virtualization, where a VMM runs in a privileged host/root partition and provides virtualization services to a unprivileged guest partition, the "paravisor" model enables a VMM to provide virtualization services from within the guest partition itself.
It can be considered a form of "virtual firmware", running at a higher privilege level than the primary guest OS.
Paravisors are quite exciting, as they enable a wide variety of useful and novel virtualization scenarios! For example: at Microsoft, OpenHCL plays a key role in enabling several important Azure scenarios:
-
Enabling existing workloads to seamlessly leverage Azure Boost (Azure's next-generation hardware accelerator), without requiring any modifications to the guest VM image.
-
Enabling existing guest operating systems to run inside Confidential VMs.
-
Powering Trusted Launch VMs - VMs that support Secure Boot, and include a vTPM.
To learn more about OpenHCL's architecture, please refer to OpenHCL Architecture.
Note: As you explore the OpenVMM repo, you may find references to the term Underhill.
Underhill was the former codename for OpenHCL, so whenever you see the term "Underhill", you can treat it as synonymous to "OpenHCL".
We are actively migrating existing code and docs away from using the term "Underhill".
Running OpenHCL
This chapter provides a high-level overview of different ways to launch and interact with OpenHCL.
OpenHCL Platforms
High-level Overview
In order to run OpenHCL, an existing host VMM must first load the OpenHCL environment into a VM, much akin to existing virtual firmware layers, like UEFI, or BIOS1.
OpenHCL is distributed as an IGVM file (Independent Guest Virtual Machine), which encapsulates all the directives and data required to launch a particular virtual machine configuration on any given virtualization stack.
At this time, the only VMMs which are able to load and host OpenHCL IGVM files are Hyper-V, and OpenVMM.
Obtaining a copy of OpenHCL
To get started, ensure you have a copy of an OpenHCL IGVM firmware image, via one of the following options:
Building OpenHCL Locally
Follow the instructions on: Building OpenHCL.
Note: At this time, OpenHCL can only be built on Linux / WSL2.
Pre-Built Binaries
If you would prefer to try OpenHCL without building it from scratch, you can download pre-built copies of OpenHCL IGVM files from OpenVMM CI.
Simply select a successful pipeline run (should have a Green checkbox), and
scroll down to select an appropriate *-openhcl-igvm artifact for your
particular architecture and operating system.
Though, unlike UEFI / BIOS, OpenHCL is loaded into a distinct, higher privilege execution context within the VM, called VTL2.
Windows - Hyper-V
Hyper-V has support for running with OpenHCL when running on Windows. This is the closest configuration to what Microsoft ships in Azure VMs, the only difference being that Azure uses Azure Host OS (as opposed to Windows Client or Windows Server).
Get a Windows version that has development support for OpenHCL
Note that Windows Client and Windows Server do not have production support for OpenHCL VMs (Microsoft does not support production workloads on OpenHCL VMs on Windows Client and Windows Server), but certain versions have development support for OpenHCL VMs (they can be used as developer platforms for the purposes of using/testing/developing OpenHCL).
Windows Client
You can use the Windows 11 2024 Update (AKA version 24H2), the third and new major update to Windows 11, as this is the first Windows version to have development support for OpenHCL VMs.
As of October 1, 2024, the Windows 11 2024 Update is available. Microsoft is taking a phased approach with its rollout. If the update is available for your device, it will download and install automatically.
Otherwise, you can get it via Windows Insider by registering with your Microsoft account and following these instructions (you can choose the "Release Preview Channel"). You may have to click the "Check for updates" button to download the latest Insider Preview build twice, and this update may take over an hour. Finally go to Settings > About to check you are on Windows 11, version 24H2 (Build 26100.1586).

Windows Server
Instructions coming soon.
Machine setup
Enable Hyper-V
Enable Hyper-V on your machine.
Enable loading from developer file
Once you get the right Windows Version, run the following command once before starting your VM. Note that this enabled loading unsigned images, and must be done as administrator.
Set-ItemProperty "HKLM:/Software/Microsoft/Windows NT/CurrentVersion/Virtualization" -Name "AllowFirmwareLoadFromFile" -Value 1 -Type DWORD | Out-Null
File access
Ensure that your OpenHCL .bin is located somewhere that vmwp.exe in your Windows host has permissions to read it (that can be in windows\system32, or another directory with wide read access).
Create a VM
Save the path of the OpenHCL .bin in a var named $Path and save the VM name you want to use in a var named $VmName.
For example:
$Path = 'C:\Windows\System32\openhcl-x64.bin'
$VmName = 'myFirstVM'
Create the Hyper-V VM
Create VM with OpenHCL (but not Trusted Launch)
Use the -GuestStateIsolationType OpenHCL parameter to New-VM. The following snippet will create a new VM that uses OpenHCL with a firmware that you specify.
# Names, directories, etc.
# cargo xflowey will do some heavy lifting for you. You can run `cargo xflowey vmm-tests --build-only --dir /mnt/q/win-vmm-tests ...` from your WSL to get images, compiled OpenHCL, etc. See [cross-compile](../../../dev_guide/getting_started/cross_compile.md) and [vmm-test](../../../dev_guide/tests/vmm.md) docs for additional info.
$repoDir = "home\<your-wsl-username-for-example>\openvmm" # for prereqs below, the path relative to the root of your WSL file system where you have cloned the openvmm repo
$VmName = "OpenHCLTestVM"
$vmOsDisk = " Q:\win-vmm-tests\osdisk.vhdx" # for step (1), the location of the OS disk for the VM. E.g. Convert-VHD Q:\win-vmm-tests\images\ubuntu-25.04-server-cloudimg-amd64.vhd -DestinationPath "Q:\win-vmm-tests\osdisk.vhdx"
$firmwareFile = "Q:\win-vmm-tests\openhcl-x64.bin" # for step (1), the location of your built OpenHCL firmware.
# Import the `hyperv.psm1` module that's used by petri, e.g.
Set-ExecutionPolicy Bypass -Scope Process # See about_Execution_Policies at https://go.microsoft.com/fwlink/?LinkID=135170.
Import-Module \\wsl.localhost\Ubuntu\$($repoDir)\petri\src\vm\hyperv\hyperv.psm1
# (1) Create a VM with OpenHCL isolation mode
$vm = New-VM $VmName -generation 2 -GuestStateIsolationType OpenHCL -VHDPath $vmOsDisk -BootDevice VHD
Set-VM -VM $vm -AutomaticCheckpointsEnabled $false
Set-VMFirmware -VM $vm -EnableSecureBoot Off # your guest image might need this, for example
Set-OpenHCLFirmware -Vm $vm -IgvmFile $firmwareFile
Create VM as a Trusted Launch VM
Enables Trusted Launch for the VM.
You can use this script with no additional instructions required (simplest path).
$vm = new-vm $VmName -generation 2 -GuestStateIsolationType TrustedLaunch
.\openhcl\Set-OpenHCL-HyperV-VM.ps1 -VM $vm -Path $Path
Create other VM types
Instructions coming soon.
Set up guest OS VHD for the VM
Running a VM will be more useful if you have a guest OS image. Given that OpenHCL is a compatibility layer, the goal is to support the same set of guest OS images that Hyper-V currently supports without a paravisor.
You can pick any existing image that you have or download one from the web, such as from Ubuntu, or any other distro that is currently supported in Hyper-V.
Add-VMHardDiskDrive -VMName $VmName -Path "<VHDX path>" -ControllerType SCSI -ControllerNumber 0 -ControllerLocation 1
Using OpenHCL to relay storage
This is a brief description to help you get started. Devs have their own scripts stashed away to make some of this easier. As we make this less tedious, we'll update this with more details.
As briefly described in the architecture overview, OpenHCL can relay (a.k.a translate) storage. It can take storage that the host presents as NVMe and show that to a guest as SCSI.
Because the core support in OpenHCL is relatively backend-agnostic, you can also show a SCSI device to VTL2 (OpenHCL) and then re-emulate that device in OpenHCL to show it again to VTL0. This is useful for test cases primarily.
While our automated test environment, petri, has good support to set this up, you need to dive into the guts of Hyper-V's WMI implementation to set this up. We have several functions used by petri in hyperv.psm1, and those are a great starting point. You can learn more about petri in the vmm test docs.
Besides reading source code, you can also find out what commands are in the petri HyperV module by running Get-Command -Module HyperV after importing it.
While these steps guide you to create a second SCSI controller, your generation 2 VM will already be booting from a SCSI controller. You could simply use that one, and your VM will boot using OpenHCL storage relay.
# Names, directories, etc.
# cargo xflowey will do some heavy lifting for you. You can run `cargo xflowey vmm-tests --build-only --dir /mnt/q/win-vmm-tests ...` from your WSL to get images, compiled OpenHCL, etc. See [cross-compile](../../../dev_guide/getting_started/cross_compile.md) and [vmm-test](../../../dev_guide/tests/vmm.md) docs for additional info.
$repoDir = "home\<your-wsl-username-for-example>\openvmm" # for prereqs below, the path relative to the root of your WSL file system where you have cloned the openvmm repo
$VmName = "OpenHCLTestVM"
$vmOsDisk = "Q:\win-vmm-tests\osdisk.vhdx" # for step (1), the location of the OS disk for the VM. E.g. Convert-VHD Q:\win-vmm-tests\images\ubuntu-25.04-server-cloudimg-amd64.vhd -DestinationPath "Q:\win-vmm-tests\osdisk.vhdx"
$firmwareFile = "Q:\win-vmm-tests\openhcl-x64.bin" # for step (1), the location of your built OpenHCL firmware.
$hostLun = 5 # for step (6) and (7), LUN on the controller presented to VTL2 from the host
$vhdPath = "Q:\win-vmm-tests\foo.vhdx" # for step (6), the path to whatever VHD is added
$guestLun = 15 # for step (7), guest visible LUN and controller ID
$guestControllerId = [guid]::NewGuid()
# Import the `hyperv.psm1` module that's used by petri, e.g.
Set-ExecutionPolicy Bypass -Scope Process # See about_Execution_Policies at https://go.microsoft.com/fwlink/?LinkID=135170.
Import-Module \\wsl.localhost\Ubuntu\$($repoDir)\petri\src\vm\hyperv\hyperv.psm1
# (1) Create a VM with OpenHCL isolation mode
$vm = New-VM $VmName -generation 2 -GuestStateIsolationType OpenHCL -VHDPath $vmOsDisk -BootDevice VHD
Set-VM -VM $vm -AutomaticCheckpointsEnabled $false
Set-VMFirmware -VM $vm -EnableSecureBoot Off # your guest image might need this, for example
Set-OpenHCLFirmware -Vm $vm -IgvmFile $firmwareFile
# (2) Use the built-in Hyper-V powershell cmdlets to create a new SCSI Controller for your VM
#
# Uses the $vm that you created above
# N.B.: Adding -Passthru is required for the cmdlet to return the controller object.
$controller = Add-VMScsiController -VM $vm -Passthru
# (3) Turn on "VMBUS Redirect", required for storage relay
Set-VMBusRedirect -Vm $vm -Enable $true
# (4) Point your new SCSI controller at OpenHCL (TargetVTL == 2)
Set-VmScsiControllerTargetVtl -Vm $vm -ControllerNumber $controller.ControllerNumber -TargetVtl 2
# (5) Get the Controller ID, this is how OpenHCL can reference this particular controller:
$controllerId = [guid](Get-VmScsiControllerIdByNumber -Vm $vm -ControllerNumber $controller.ControllerNumber)
if (-not $controllerId) {
throw "Failed to resolve SCSI controller ID; ensure the controller exists and the HyperV module is imported."
}
# (6) Attach a VHD to the host
# e.g., New-VHD -Path $vhdPath -SizeBytes 1gb -Dynamic
Add-VMHardDiskDrive -VM $vm -ControllerType SCSI -ControllerNumber $controller.ControllerNumber -ControllerLocation $hostLun -Path $vhdPath
# (7) Craft settings
# Build Base-namespace VTL2 settings (JSON) with:
# * 1 SCSI controller (guest-visible instance id: $guestControllerId)
# * 1 disk at guest LUN $guestLun
# * Backed by a single PhysicalDevice of type vscsi with vsid $controllerId
# and sub_device_path (host LUN) $hostLun
$settings = @{
version = "V1"
dynamic = @{
storage_controllers = @(
@{
instance_id = $guestControllerId.ToString()
protocol = "SCSI"
luns = @(
@{
location = [uint32]$guestLun
device_id = ([guid]::NewGuid()).ToString()
vendor_id = "OpenVMM"
product_id = "Disk"
product_revision_level = "1.0"
serial_number = "0"
model_number = "1"
physical_devices = @{
type = "single"
device = @{
device_type = "vscsi"
device_path = $controllerId.ToString()
sub_device_path = [uint32]$hostLun
}
}
is_dvd = $false
chunk_size_in_kb = 0
}
)
}
)
}
}
$settingsFile = Join-Path $env:TEMP "vtl2settings.json"
$settings | ConvertTo-Json -Depth 10 | Set-Content -Path $settingsFile -Encoding UTF8
# (8) Set settings
Set-Vtl2Settings -VmId $vm.Id -Namespace "Base" -SettingsFile $settingsFile
# (9) start your VM
Start-VM -VM $vm
Windows - OpenVMM
OpenVMM currently has basic support for running with OpenHCL when run on Windows with WHP, with some caveats:
- Performance is not great due to the extra overhead of OpenVMM modeling VTLs, not the hypervisor.
- Not all hypercalls are implemented, only the set used by OpenHCL.
- Not all OpenHCL configuration and runtime management APIs are exposed / wired-up.
These are all caveats that can (and will) be overcome with additional investments into OpenVMM.
That said: running OpenHCL on OpenVMM is currently considered to be a dev-only workflow, not suitable for production use.
To get a more complete and accurate experience of what OpenHCL's production runtime characteristics and user ergonomics are like, we currently suggest running OpenHCL on Hyper-V.
Examples
These examples assume basic familiarity with the OpenVMM command line, and a willingness to deal with OpenVMM's various "rough edges" (as described in Getting Started: OpenVMM).
These examples all use cargo run --, with the assumption that you are a
developer building your own copy of OpenVMM locally!
To run these examples using a pre-compiled copy of OpenVMM, swap cargo run -- with /path/to/openvmm.
If you run into any issues, please refer to OpenVMM: Troubleshooting, and/or OpenHCL: Troubleshooting.
Preface: Using ohcldiag-dev
Add support for ohcldiag-dev by specifying the --vtl2-vsock-path option at vm
launch. This will create a Unix socket that the ohcldiag-dev binary can connect to by
specifying the path to the unix socket. By default, the socket is created in the
temp directory with path ohcldiag-dev. For example, running via powershell:
cargo run -p ohcldiag-dev -- $env:temp\ohcldiag-dev kmsg
Linux direct
Linux direct will work with an interactive console available via COM ports hosted in VTL2, relayed over VMBUS like on Hyper-V. Build a Linux direct IGVM file and launch with the following command line to enable COM0 and COM1 for VTL0:
cargo run -- --hv --vtl2 --igvm openhcl-x64.bin --com3 "term,name=VTL2 OpenHCL" -m 2GB --vmbus-com1-serial "term,name=VTL0 Linux" --vmbus-com2-serial "term,name=COM2" --vtl2-vsock-path $env:temp\ohcldiag-dev
This will launch OpenVMM in VTL2 mode using Windows Terminal to display the
output of the serial ports. You can replace term with term=<path to exe> to use your
favorite shell and by default OpenVMM will use cmd.exe. A vsock window can be opened
using the OpenVMM terminal on windows using v 9980 or whichever hvsock port is
configured to allow consoles for OpenHCL.
Vtl2 VMBus Support
OpenHCL run under OpenVMM can act as the VMBus server to VTL0. Additionally, OpenHCL can be configured to forward offers made by OpenVMM to VTL0.
To run OpenVMM and OpenHCL with VMBus host relay support:
--vmbus-redirect
Assigning MANA devices to VTL2
OpenHCL can be assigned a MANA NIC to VTL2, and expose a VMBus NIC to the guest in VTL0. Expose it by adding the following:
--net uh:consomme --vmbus-redirect
Assigning SCSI devices to VTL2
You can assign a SCSI disk to VTL2 and have OpenHCL reassign it to VTL0:
--disk file:ubuntu.img,uh --vmbus-redirect
Assigning NVME devices to VTL2
You can assign an NVME disk to VTL2 and have OpenHCL relay it to VTL0 as a VMBus scsi device:
--disk mem:1G,uh-nvme --vmbus-redirect
Linux
Currently, OpenHCL cannot be used on Linux hosts, primarily due to limitations in KVM (or our imagination). We would love to improve this, and we would accept contributions that get this working.
Technical Details
The main challenge is that OpenHCL needs to run in an environment where it can trap and emulate privileged instructions from the guest OS. It also benefits from the host being able to target interrupts directly into the guest OS, without relaying them through OpenHCL.
On Windows, this is achieved via Hyper-V's VTL support, even when leveraging isolation technologies like SNP and TDX. As of writing this, KVM does not yet support the required primitives for this.
Here are some approaches we can take to close the gap:
-
Use KVM's nested virtualization support. Launch an ordinary VM to run OpenHCL, modified to launch the guest OS in a nested VM. This won't be as fast as OpenHCL in Hyper-V, but it will allow a simple development environment on existing Linux kernels.
-
Extend KVM to support Hyper-V-style VTLs, to reach parity with Hyper-V, even in non-confidential VMs.
-
Extend KVM to fully support multiple VMPLs on SNP machines, and update OpenHCL to support using architectural GHCB calls to switch VMPLs, rather than Hyper-V-specific hypercalls.
-
Update OpenHCL to support TDX without Hyper-V-specific hypercalls. Optionally, extend KVM to model TDX L2s as VTLs so that the host can target interrupts to the guest directly.
Additionally, OpenHCL currently relies on Hyper-V communication devices for guest configuration and runtime services. This ties OpenHCL to the OpenVMM or Hyper-V VMMs. We are looking for ways to support alternatives for use with other VMMs such as qemu.
If you are interested in helping with any of this, please let us know.
OpenHCL Troubleshooting
This page includes a miscellaneous collection of troubleshooting tips for common issues you may encounter when running OpenHCL.
If you are still running into issues, consider filing an issue on the OpenVMM GitHub Issue tracker.
[Hyper-V] VTL2/VTL0 failed to start
VTL2/VTL0 fails to boot is when either VTL2 or VTL0 has crashed. When the crash happens, they will emit an event to the Hyper-V worker channel.
First, check Hyper-V worker events at Applications and Services Logs -> Microsoft -> Windows -> Hyper-V-Worker-Admin
Alternatively, some queries you can use to get Hyper-V-Worker logs:
- Display the
{n}most recent events -wevtutil qe Microsoft-Windows-Hyper-V-Worker-Admin /c:{n} /rd:true /f:text - Export events to file -
wevtutil epl Microsoft-Windows-Hyper-V-Worker-Admin C:\vtl2_0_crash.evtx
Checking OpenHCL logging output
OpenHCL logging output can be useful for debugging issues with startup or runtime behavior.
See OpenHCL Tracing for more details about how to enable OpenHCL logging.
DeviceTree errors or warnings in the VTL2 kernel log
- Retrieve the DeviceTree blob from OpenHCL:
uhdiag-dev.exe linux-uhvm00 file --file-path "/sys/firmware/fdt" > uh.dtb
- Install the DeviceTree compiler and convert the blob to the textual representation:
sudo apt-get install dtc
dtc -I dtb -o uh.dts uh.dtb
Check on the errors and warnings and should any have been produced, fix them in the DeviceTree generation code. If that doesn't resolve the issues, inspect the DT parsing code in the Linux kernel.
Next Steps
To learn more about how OpenHCL works, and how to interact with it:
| Reference: OpenHCL Features | Configure and interact with OpenHCL |
| Dev Guide: Building OpenHCL | Build OpenHCL locally |
| Reference: OpenHCL Architecture | Understand how OpenHCL works "under the hood" |
Getting Started (for Developers)
This chapter discusses all the basic steps required to begin building code in the OpenVMM project.
By the end of this chapter, you will have:
- Cloned the OpenVMM git repo
- Installed all required pre-build dependencies (e.g: Rust)
- Built local copies of both OpenVMM and OpenHCL
- (optionally) Set up a suggested VSCode-based development environment
Aside: What is HvLite? Underhill?
As you explore the OpenVMM repo, you may find references to things called HvLite and Underhill.
Simply put:
- OpenVMM is synonymous with HvLite
- OpenHCL is synonymous with Underhill
HvLite and Underhill were former Microsoft-internal codenames for OpenVMM and OpenHCL.
Migrating all existing code and documentation away from these codewords is not an overnight process, and it's quite likely these terms will linger in various code comments, variable names, library names, etc... the forseeable future.
Getting started on Linux / WSL2
This page provides instructions for installing the necessary dependencies to build OpenVMM or OpenHCL on Linux / WSL2.
[WSL2] Installing WSL2
To install Windows Subsystem for Linux, run the following command in an elevated Powershell window:
PS> wsl --install
This should install WSL2 using the default Ubuntu linux distribution. You can check that the installation completed successfully by running the following command in a Powershell window.
PS> wsl -l -v
NAME STATE VERSION
* Ubuntu Running 2
Once that command has completed, you will need to open WSL to complete the
installation and set your password. You can open WSL by typing wsl or bash
into Command Prompt or Powershell, or by opening the "Ubuntu" Windows Terminal
profile that should have been created.
If you intend to cross-compile OpenVMM for Windows, please ensure you are running a recent version of Windows 11. Windows 10 is no longer supported as a development platform, due to needed WHP APIs.
All subsequent commands on this page must be run within WSL2.
Installing Rust
To build OpenVMM or OpenHCL, you first need to install Rust.
The OpenVMM project actively tracks the latest stable release of Rust, though it may take a week or two after a new stable is released until OpenVMM switches over to it.
Please follow the official instructions to do so.
[Linux] Additional Dependencies
On Linux, there are various other dependencies you will need depending on what you're working on. On Debian-based distros such as Ubuntu, running the following command within WSL will install these dependencies.
In the future, it is likely that this step will be folded into the
cargo xflowey restore-packages command.
$ sudo apt install \
binutils \
build-essential \
gcc-aarch64-linux-gnu \
libssl-dev \
pkg-config
Cloning the OpenVMM source
If using WSL2: Do NOT clone the repo into Windows then try to access said clone from Linux! It will result in serious performance issues, and may break certain functionality (e.g: cross-compiling Windows binaries).
cd ~/src/
git clone https://github.com/microsoft/openvmm.git
Next Steps
You are now ready to build OpenVMM or OpenHCL!
Getting started on Windows
This page provides instructions for installing the necessary dependencies to build OpenVMM on Windows.
We strongly suggest using WSL2 for OpenVMM development, rather than developing on Windows directly.
Developing in WSL2 offers a smoother development experience, while still allowing you to build and run OpenVMM on Windows through the use of cross compilation.
Additionally, it allows you to have a single clone of the OpenVMM repo suitable for both OpenVMM and OpenHCL development.
You must be running a recent version of Windows 11. Windows 10 is no longer supported as a development platform, due to needed WHP APIs.
NOTE: OpenHCL does NOT build on Windows.
If you are interested in building OpenHCL, please follow the getting started guide for Linux / WSL2.
Installing Rust
To build OpenVMM, you first need to install Rust.
The OpenVMM project actively tracks the latest stable release of Rust, though it may take a week or two after a new stable is released until OpenVMM switches over to it.
Please follow the official instructions to do so.
Visual Studio C++ Build Tools and Windows SDK
If you don't already have it, you will need to install Visual Studio C++ Build tools or Visual Studio with the components "Desktop Development for C++" and the Windows SDK. Windows 11 SDK version 26100 is the latest version as of this update, but you should install the newest version if there is a newer version.
The C++ build tools can be installed via Visual Studio Installer -> Modify -> Individual Components
-> MSVC v143 - VS 2022 C++ x64/x86 build tools (latest).
The Windows SDK can be installed via Visual Studio Installer -> Modify -> Individual Components
-> Windows 11 SDK (10.0.26100.0).
The C++ build tools and Windows SDK can be installed at the same time.
Or, you can install the tool via the powershell command below.
PS> winget install Microsoft.VisualStudio.2022.Community --override "--quiet --add Microsoft.VisualStudio.Component.VC.Tools.x86.x64 --add Microsoft.VisualStudio.Component.Windows11SDK.26100"
Aarch64 support
To build ARM64, you need an additional dependency.
This can be installed via Visual Studio Installer -> Modify -> Individual Components
-> MSVC v143 - VS 2022 C++ ARM64/ARM64EC build tools (latest).
Or, you can install the tool via the powershell command below.
PS> winget install Microsoft.VisualStudio.2022.Community --override "--quiet --add Microsoft.VisualStudio.Component.VC.Tools.ARM64"
Cloning the OpenVMM source
If you haven't already installed git, you can download it
here.
PS> git clone https://github.com/microsoft/openvmm.git
Next Steps
You are now ready to build OpenVMM!
Getting started via Dev Container
This page provides instructions for setting up a development environment using the repo provided Dev Container configuration for local development or development using GitHub Codespaces.
The repo provides an Ubuntu devcontainer.json that installs Rust and the
supported targets for the project.
Developing using a GitHub Codespace
Either create a GitHub Codespace via your fork by clicking on the Code box, or
visit the link here and select your fork
and branch.
If you plan on using rust-analyzer or doing any sort of dev work, it's recommended to use an 8 core SKU or beefier.
More documentation can be found at the official GitHub docs.
Developing using a local dev container
This will use Docker + the dev container vscode extension to launch the repo
provided devcontainer.json on your local machine.
Follow the install instructions outlined here.
From there, use the dev container extension in vscode to create a new dev container for the repository.
It's recommended to clone the repo inside the dev container using the Dev Containers: Clone Repository Inside Container Volume... command, as the
filesystem otherwise will be very slow over the bind mount, which will make your
builds & rust-analyzer very slow.
More documentation can be found at the official vscode docs.
Customizing your dev container
Both GitHub codespaces and local dev containers support dotfile repos which can be used to run personalized install scripts like installing your favorite tools and shells, and copying over your dotfiles and configuration.
For codespaces, see the documentation here. For dev containers, see the documentation here.
You can use the same dotfiles repo for both, but note that codespaces has a few more limitations outlined in their documentation.
Building OpenVMM
Prerequisites:
It is strongly suggested that you use WSL2, and cross compile for Windows when necessary.
Build Dependencies
OpenVMM currently requires a handful of external dependencies to be present in
order to properly build / run. e.g: a copy of protoc to compile Protobuf
files, a copy of the mu_msvm UEFI firmware, some test linux kernels, etc...
Running the following command will fetch and unpack these various artifacts into the correct locations within the repo:
cargo xflowey restore-packages
If you intend to cross-compile, refer to the command's --help for additional
options related to downloading packages for other architectures.
Building
OpenVMM uses the standard Rust build system, cargo.
To build OpenVMM, simply run:
cargo build
Note that certain features may require compiling with additional --feature
flags.
Troubleshooting
This section documents some common errors you may encounter while building OpenVMM.
If you are still running into issues, consider filing an issue on the OpenVMM GitHub Issue tracker.
failed to invoke protoc
Error:
error: failed to run custom build command for `inspect_proto v0.0.0 (/home/daprilik/src/openvmm/support/inspect_proto)`
Caused by:
process didn't exit successfully: `/home/daprilik/src/openvmm/target/debug/build/inspect_proto-e959f9d63c672ccc/build-script-build` (exit status: 101)
--- stderr
thread 'main' panicked at support/inspect_proto/build.rs:23:10:
called `Result::unwrap()` on an `Err` value: Custom { kind: NotFound, error: "failed to invoke protoc (hint: https://docs.rs/prost-build/#sourcing-protoc): (path: \"/home/daprilik/src/openvmm/.packages/Google.Protobuf.Tools/tools/protoc\"): No such file or directory (os error 2)" }
note: run with `RUST_BACKTRACE=1` environment variable to display a backtrace
warning: build failed, waiting for other jobs to finish...
Note: the specific package that throws this error may vary, and may not always be inspect_proto
Solution:
You attempted to build OpenVMM without first restoring necessary packages.
Please run cargo xflowey restore-packages, and try again.
use of unstable library feature
Error:
error[E0658]: use of unstable library feature 'absolute_path'
--> flowey/flowey/src/lib.rs:37:17
|
37 | std::path::absolute(self)
| ^^^^^^^^^^^^^^^^^^^
|
= note: see issue #92750 <https://github.com/rust-lang/rust/issues/92750> for more information
For more information about this error, try `rustc --explain E0658`.
error: could not compile `flowey` (lib) due to previous error
Solution:
Install Rust using the official instructions for Linux or Windows.
Building OpenHCL
Prerequisites:
Reminder: OpenHCL cannot currently be built on Windows hosts!
An OpenHCL IGVM firmware image is composed of several distinct binaries and
artifacts. For example: the openvmm_hcl usermode binary, the OpenHCL boot
shim, the OpenHCL Linux kernel and initrd, etc....
Some of these components are built directly out of the OpenVMM repo, whereas others must be downloaded as pre-built artifacts from other associated repos. Various tools and scripts will then transform, package, and re-package these artifacts into a final OpenHCL IGVM firmware binary.
Fortunately, we don't expect you do to all those steps manually!
All the complexity of installing the correct system dependencies, building the
right binaries, downloading the right artifacts, etc... is neatly encapsulated
behind a single cargo xflowey build-igvm command, which orchestrates the
entire end-to-end OpenHCL build process.
Using the build-igvm flow is as simple as running:
cargo xflowey build-igvm [RECIPE]
The first build will take some time as all the dependencies are installed/downloaded/built.
Note: At this time, OpenHCL can only be built on Linux (or WSL2)!
A "recipe" corresponds to one of the pre-defined IGVM SKUs that are actively supported and tested in OpenVMM's build infrastructure.
A single recipe encodes all the details of what goes into an individual IGVM
file, such as what build flags openvmm_hcl should be built with, what goes
into a VTL2 initrd, what igvmfilegen manifest is being used, etc...
- e.g:
x64, for a "standard" x64 IGVM - e.g:
aarch64, for a "standard" aarch64 IGVM - e.g:
x64-cvm, for a x64 CVM IGVM - e.g:
x64-test-linux-direct, for x64 IGVM booting a test linux direct image - for a full list of available recipes, please run
cargo xflowey build-igvm --help
New recipes can be added by modifying the build-igvm source code.
Build output is then binplaced to: flowey-out/artifacts/build-igvm/{release-mode}/{recipe}/openhcl-{recipe}.bin
So, for example:
cargo xflowey build-igvm x64-cvm
# output: flowey-out/artifacts/build-igvm/debug/x64-cvm/openhcl-x64-cvm.bin
cargo xflowey build-igvm x64 --release
# output: flowey-out/artifacts/build-igvm/release/x64/openhcl-x64.bin
cargo xflowey build-igvm is designed to be used as part of the
developer inner-loop, and does NOT have a stable CLI suitable for CI or any
other form of production automation!
In-tree pipelines and automation should interface with the underlying flowey
infrastructure that powers cargo xflowey build-igvm, without relying on
the details of its CLI.
Building ohcldiag-dev
ohcldiag-dev is typically built as a Windows binary.
This can be done directly from Windows, or using cross-compilation from WSL2.
The command to build ohcldiag-dev is simply:
# you may need to run `rustup target add x86_64-pc-windows-msvc` first
cargo build -p ohcldiag-dev --target x86_64-pc-windows-msvc
Note: Thanks to x86 emulation built into Windows, ohcldiag-dev.exe that is
built for x64 Windows will work on Aarch64 Windows as well.
Troubleshooting
This section documents some common errors you may encounter while building OpenHCL.
If you are still running into issues, consider filing an issue on the OpenVMM GitHub Issue tracker.
Help! The build failed due to a missing dependency
If you don't mind having xflowey install some dependencies globally on your
machine (i.e: via apt install, or rustup toolchain add), you can pass
--auto-install-deps to your invocation of build-igvm.
Alternatively - build-igvm should emit useful human-readable error messages
when it encounters a dependency that isn't installed, with a suggestion on how
to install it.
If it doesn't - please file an Issue!
Help! Everything is rebuilding even though I only made a small change
Cargo's target triple handling can be a bit buggy. Try running with:
CARGO_BUILD_TARGET=x86_64-unknown-linux-gnu cargo build-igvm [RECIPE]
or adding the below to your .bashrc:
export CARGO_BUILD_TARGET=x86_64-unknown-linux-gnu
Build Customization
Aside from building IGVM files corresponding the the built-in IGVM recipes,
build-igvm also offers a plethora of customization options for developers who
wish to build specialized custom IGVM files for local testing.
Some examples of potentially useful customization include:
-
--override-manifest: Override the recipe'sigvmfilegenmanifest file via, in order to tweak different kernel command line options, different VTL0 boot configuration, or different VTL2 memory sizes. -
--custom-openvmm-hcl: Specify a pre-builtopenvmm_hclbinary. This is useful in case you have already built it with some custom settings, e.g.:cargo build --target x86_64-unknown-linux-musl -p openvmm_hcl --features myfeature cargo xflowey build-igvm x64 --custom-openvmm-hcl target/x86_64-unknown-linux-musl/debug/openvmm_hcl -
Specify a custom VTL2 kernel
vmlinux/Image, instead of using a pre-packed stable/dev kernel.cargo xflowey build-igvm x64 --custom-kernel path/to/my/prebuilt/vmlinux
For a full list of available customizations, refer to build-igvm --help.
Advanced
Depending on what you're doing, you may need to build the individual components that go into an OpenHCL IGVM build.
Our flowey-based pipelines handle the complexities of properly invoking and
orchestrating the various individual build tools / scripts used to construct
IGVM files, but a sufficiently motivated user can go through these steps
manually.
Please consult the source code for cargo xflowey build-igvm for a breakdown of
all build steps and available customization options.
Note that the canonical "source of truth" for how to build end-to-end OpenHCL IGVM files are these build scripts themselves, and the specific flow is subject to change over time!
Building a custom OpenHCL Linux Kernel
This step is NOT required in order to build OpenHCL!
Unless you have a specific reason, it is strongly recommended to stick to the pre-built Kernel image which is automatically downloaded as part of the OpenHCL build process.
Cloning the kernel repository
If you need to rebuild the kernel, the sources are available in the OHCL-Linux-Kernel repo :
- the main branch is product/hcl-main/6.6,
- the dev branch is project/hcl-dev/6.6.
Unless you need the entire repo history, cloning just one branch and depth = 1, saves
significant time and disk space:
git clone https://github.com/microsoft/OHCL-Linux-Kernel.git -b product/hcl-main/6.6 --depth=1
Cloning under Windows is likely to fail due to some files using names that Windows reserves, e.g. aux.c, and
NTFS being non case-sensitive by default as there are few files in the Linux kernel repo whose names differ
in their case only. To clone successfully under Windows, need a fix in ntdll (merged in Ni?),
and a case-sensitive NTFS partition. Best to start with the default WSL2 if there is no existing working setup.
Building the kernel locally
The following instructions for building the kernel locally target the Ubuntu distributions.
In order to build on rpm-based systems the only changes are likely to be the way the package
manager is invoked and installing the kernel-devel package instead of what is needed for
Ubuntu.
The paths below are relative to the cloned kernel repository root.
Do once for every machine that hasn't run this step successfully:
./Microsoft/install-deps.sh
If you plan to use your custom kernel to work with confidential VMs, you need to enable a few more options in the kernel. Do once after cloning the kernel repository or every time you remove local changes from your kernel configuration file:
./Microsoft/merge-cvm-config.sh
Every time the kernel needs to be rebuilt:
./Microsoft/build-hcl-kernel.sh
The output directory is ./out, it contains the kernel binary, the kernel modules,
and the debug symbols, and cargo xflowey build-igvm can be pointed to it to use
as a source of the kernel binary and the modules.
In the case you are iterating on a change, install ccache
for decreasing the kernel build time significantly, might be close to an order of
magnitude. To use the compiler cache, prepend CC="ccache gcc" to the build command.
To see if the cache integrates itself into the toolchain:
host:~$ which gcc
/usr/lib64/ccache/gcc
Suggested Dev Environment
Prerequisites:
- One of:
- One of:
This page is for those interested in actively iterating on OpenVMM or OpenHCL.
Setting up VSCode
These instructions assume you're using VSCode.
If you're using a different development environment, we nonetheless suggest reading through this section, so you can enable similar settings in whatever editor / IDE you happen to be using.
Just want the recommended editor settings? Put this in openvmm/.vscode/settings.json:
{
"rust-analyzer.linkedProjects": [
"Cargo.toml",
],
"rust-analyzer.cargo.targetDir": true,
"rust-analyzer.imports.granularity.group": "item",
"rust-analyzer.imports.group.enable": false,
"[rust]": {
"editor.formatOnSave": true
},
}
[WSL2] Connecting to WSL using VSCode
When using Visual Studio Code with WSL, be sure to use the
WSL extension
instead of accessing your files using the \\wsl.localhost share (the repo
should be cloned in the WSL filesystem, as mentioned in the WSL getting started
guide). This will ensure that all VSCode extensions and features to work properly.
Once the extension is installed, click the blue arrows in the bottom left corner and select "Connect to WSL". Then open the folder you cloned the repository into. More information is available here.
Configuring rust-analyzer
rust-analyzer provides IDE-like functionality when writing Rust code (e.g: autocomplete, jump to definition, refactoring, etc...). It is a massive productivity multiplier when working with Rust code, and it would be a very bad idea to work in the OpenVMM repo without having it set up correctly.
Check out the rust-analyzer manual for a comprehensive overview of rust-analyzer's features.
Once installed, we suggest you specify the following additional configuration
options in the OpenVMM workspace's .vscode/settings.json file:
{
"rust-analyzer.linkedProjects": [
"Cargo.toml",
]
}
(Strongly Suggested) Avoiding cache invalidation
To avoid unnecessary re-builds or lock-contention in the build directory between rust-analyzer and manual builds, set the following configuration option to give rust-analyzer a separate target directory:
{
"rust-analyzer.cargo.targetDir": true,
}
(Strongly Suggested) Disable nested imports
When auto-importing deps, rust-analyzer defaults to nesting imports, which isn't the OpenVMM convention.
This can be changed to one-dep-per-line by specifying the following settings:
{
"rust-analyzer.imports.granularity.group": "item",
"rust-analyzer.imports.group.enable": false,
}
Enabling clippy
CI will fail if the code is not clippy-clean. Clippy is a linter that helps catch common mistakes and improves the quality of our Rust code.
By default, rust-analyzer will use cargo check to lint code, but it can be
configured to use cargo clippy instead:
{
"rust-analyzer.check.command": "clippy",
}
Enabling Format on Save
CI will fail if code is not formatted with rustfmt.
You can enable the "format on save" option in VSCode to automatically run
rustfmt whenever you save a file:
{
"[rust]": {
"editor.formatOnSave": true
},
}
Enhanced "Enter"
rust-analyzer can override the "Enter" key to make it smarter:
- "Enter" inside triple-slash comments automatically inserts
/// - "Enter" in the middle or after a trailing space in
//inserts// - "Enter" inside
//!doc comments automatically inserts//! - "Enter" after
{indents contents and closing}of single-line block
This action needs to be assigned to shortcut explicitly, which can be done by
adding the following line to keybindings.json:
// must be put into keybindings.json, NOT .vscode/settings.json!
{
"key": "Enter",
"command": "rust-analyzer.onEnter",
"when": "editorTextFocus && !suggestWidgetVisible && editorLangId == rust"
}
GitHub Pull Request Integration
As the repo is hosted on GitHub, you might find convenient to use the GitHub Pull Request VSCode extension. That allows working through the PR feedback and issues without leaving the comfort of VSCode.
(Possibly Useful) Enabling 'house-rules' formatting on-save
Aside from using rustfmt, the OpenVMM project also relies on a handful of
extra formatting "house rules". e.g: enfocing the presence of copyright headers,
enforcing single-trailing newlines, etc...
CI will fail if files are not formatted with cargo xtask fmt house-rules.
In general, there are 3 ways to fix "house rules" related lints:
- Manually fixing issues in response to automated feedback
- Invoking
cargo xtask fmt house-rules --fixto fix the whole project - Invoking
cargo xtask fmt house-rules --fix [FILE]to fix a given file
If you would prefer having "house-rules" enfoced whenever you save a file in
VSCode, you can install the
RunOnSave
extension, and add the following configuration to .vscode/settings.json:
{
"emeraldwalk.runonsave": {
"commands": [
{
"match": ".*",
"cmd": "cd ${workspaceFolder}"
},
{
"match": ".*",
"isAsync": true,
"cmd": "$(cat ./target/xtask-path) --run-on-save fmt house-rules --fix ${file}"
}
]
},
}
Setting up pre-commit and pre-push hooks
It's never fun having CI reject your changes due to some minor formatting issue,
especially when it's super quick to run those formatting checks locally. Running
cargo xtask fmt before pushing up your code is quick and easy, and will save
you the annoyance of wrestling with formatting check-in gates!
Of course, it's very easy to forget to run cargo xtask fmt after making code
changes, but thankfully, you can set up some git hooks
that will do this for you automatically!
You can run cargo xtask install-git-hooks --help for more details on what
hooks are available and their various configuration options, but for most users,
we suggest the following config:
cargo xtask install-git-hooks --pre-push --with-fmt=yes
And you'll be all set!
If you're worried about time, the pre-push hook should only take ~5
seconds to run locally. That's far better than waiting ~20+ minutes only
for CI to fail on your pull request.
[WSL2] Cross Compiling from WSL2 to Windows
You may also want to set up cross compiling in WSL2 to you can build for both Windows and Linux in one dev environemnt.
[WSL2] Cross Compiling from WSL2 to Windows
Setting up cross compilation is very useful, as it allows using the same repo cloned in WSL2 to both develop OpenHCL, as well as launch it via OpenVMM via the WHP backend.
Required Dependencies
Note that this requires some additional dependencies, described below.
Windows deps
Visual Studio build tools must be installed, along with the Windows SDK. This is the same as what's required to build OpenVMM on windows.
WSL deps
The msvc target x86_64-pc-windows-msvc must be installed for the toolchain
being used in WSL. This can be added by doing the following:
rustup target add x86_64-pc-windows-msvc
Additional build tools must be installed as well. If your distro has LLVM 14 available (Ubuntu 22.04 or newer):
sudo apt install clang-tools-14 lld-14 llvm-dev
Otherwise, follow the steps at https://apt.llvm.org/ to install a specific
version, by adding the correct apt repos. Note that you must install
clang-tools-14 as default clang-14 uses gcc style arguments, where
clang-cl-14 uses msvc style arguments. You can use their helper script as
well:
wget https://apt.llvm.org/llvm.sh
chmod +x llvm.sh
sudo ./llvm.sh 14
sudo apt install clang-tools-14
Setting up the terminal environment
Source the build_support/setup_windows_cross.sh script from your terminal
instance. For example, the following script will do this along with setting a
default cargo build target:
#!/bin/bash
# Setup environment and windows cross tooling.
export CARGO_BUILD_TARGET=x86_64-unknown-linux-gnu
cd path/to/openvmm || exit
. build_support/setup_windows_cross.sh
exec "$SHELL"
For developers using shells other than bash, you may need to run the
setup_windows_cross.sh script in bash then launch your shell in order to get
the correct environment variables.
Editing with vscode
You can have rust-analyzer target Windows, which will allow you to use the same
repo for OpenHCL, Linux, and Windows changes, but the vscode remote server
must be launched from the terminal window that sourced the setup script. You can
do this by closing all vscode windows then opening your workspace with
code <path to workspace> in your terminal.
Add the following to your workspace settings for a vscode workspace dedicated to Windows:
"settings": {
"rust-analyzer.cargo.target": "x86_64-pc-windows-msvc"
}
Running Windows OpenVMM from within WSL
You can build and run the windows version of OpenVMM by overriding the target
field of cargo commands, via --target x86_64-pc-windows-msvc. For example, the
following command will run OpenVMM with WHP:
cargo run --target x86_64-pc-windows-msvc
You can optionally set cargo aliases for this so that you don't have to type out
the full target every time. Add the following to your ~/.cargo/config.toml:
[alias]
winbuild = "build --target x86_64-pc-windows-msvc"
wincheck = "check --target x86_64-pc-windows-msvc"
winclippy = "clippy --target x86_64-pc-windows-msvc"
windoc = "doc --target x86_64-pc-windows-msvc"
winrun = "run --target x86_64-pc-windows-msvc"
wintest = "test --target x86_64-pc-windows-msvc"
You can then run the windows version of OpenVMM by running:
cargo winrun
OpenVMM configures some environment variables that specify the default Linux kernel, initrd, and UEFI firmware. To make those variables available in Windows, run the following:
export WSLENV=$WSLENV:X86_64_OPENVMM_LINUX_DIRECT_KERNEL:X86_64_OPENVMM_LINUX_DIRECT_INITRD:AARCH64_OPENVMM_LINUX_DIRECT_KERNEL:AARCH64_OPENVMM_LINUX_DIRECT_INITRD:X86_64_OPENVMM_UEFI_FIRMWARE:AARCH64_OPENVMM_UEFI_FIRMWARE:RUST_BACKTRACE
Speeding up Windows OpenVMM launch
Due to filesystem limitations on WSL, launching OpenVMM directly will be somewhat slow. Instead, you can copy the built binaries to a location on in the Windows filesystem and then launch them via WSL.
Quite a few folks working on the OpenVMM project have hacked together personal helper scripts to automate this process. Here is one example: (update the variables at the top of the file as necessary.)
#!/bin/bash
# build & run script for openhcl testing with openvmm
set -e
args="-m 4GB -p 4"
copy_symbols=true
copy_remote=false
windows_temp="/mnt/e/cross"
windows_temp_win="E:\\cross"
remote_temp="\\\\<remote_computer>\\cross"
windows_enlistment="/mnt/e/openvmm"
disk_path="$windows_temp_win\\disk.vhdx"
uefi_firmware="$windows_temp_win\\MSVM.fd"
if [[ $# -lt 2 ]]; then
echo "Usage: $0 <build|run|ohcldiag-dev> <x64|aarch64>..."
exit 1
fi
if [[ $2 == "aarch64" ]]; then
arch="aarch64"
short_arch="aarch64"
elif [[ $2 == "x64" ]]; then
arch="x86_64"
short_arch="x64"
else
echo "Unknown arch: $2"
echo "Usage: $0 $1 <x64|aarch64>"
exit 2
fi
uhdiag_path="$windows_temp_win\\uhdiag"
openvmm_path="$windows_temp/openvmm.exe"
windows_openvmm="$windows_temp/openvmm"
base_igvm="flowey-out/artifacts/build-igvm"
win_target="$arch-pc-windows-msvc"
base_win="target/$win_target/debug"
if [[ $1 == "build" || $1 == "run" ]]; then
build_args="--target $arch-pc-windows-msvc"
if [[ $3 == "vmm" ]]; then
if [[ $4 == "uefi" ]]; then
args+=" --uefi --uefi-firmware $uefi_firmware --disk memdiff:$disk_path"
elif [[ $4 == "linux" ]]; then
args+=""
else
echo "Unknown load mode: $4"
echo "Usage: $0 $1 $2 $3 <uefi|linux>"
exit 2
fi
elif [[ $3 == "hcl" ]]; then
if [[ $4 == "uefi" ]]; then
recipe="$short_arch"
args+=" --disk memdiff:$disk_path --gfx --vmbus-com1-serial term --uefi-console-mode com1 --uefi"
elif [[ $4 == "linux" ]]; then
recipe="$short_arch-test-linux-direct"
args+=" --vmbus-com1-serial term --vmbus-com2-serial term"
else
echo "Unknown load mode: $4"
echo "Usage: $0 $1 $2 $3 <uefi|linux>"
exit 2
fi
ohcl_name="openhcl-$recipe.bin"
ohcl_path="$base_igvm/debug/$recipe"
ohcl_symbols="openvmm_hcl"
args+=" --hv --vtl2 --igvm $windows_temp_win\\$ohcl_name --vtl2-vsock-path $uhdiag_path --com3 term"
echo "Building OpenHCL..."
(
set -x
cargo xflowey build-igvm $recipe
)
else
echo "Unknown package: $2"
echo "Usage: $0 $1 <vmm|hcl>"
exit 2
fi
echo
if [[ $5 == "unstable" ]]; then
build_args+=" --features unstable_whp"
fi
echo "Building openvmm..."
(
set -x
cargo build $build_args
)
echo
# Copy to Windows
echo "Copying to windows"
if [[ $3 == "hcl" ]]; then
(
set -x
cp -u "$ohcl_path/$ohcl_name" "$windows_temp/$ohcl_name" -f
mkdir -p "$windows_enlistment/$ohcl_path"
cp -u "$ohcl_path/$ohcl_name" "$windows_enlistment/$ohcl_path/$ohcl_name" -f
)
if $copy_remote; then
(
set -x
powershell.exe Copy-Item "$windows_temp_win\\$ohcl_name" "$remote_temp\\$ohcl_name" -Force
)
fi
if $copy_symbols; then
(
set -x
cp -u "$ohcl_path/$ohcl_symbols" "$windows_temp/openvmm_hcl" -f
cp -u "$ohcl_path/$ohcl_symbols.dbg" "$windows_temp/openvmm_hcl.dbg" -f
)
fi
fi
(
set -x
cp -u "$base_win/openvmm.exe" $openvmm_path -f
mkdir -p "$windows_enlistment/$base_win"
cp -u "$base_win/openvmm.exe" "$windows_enlistment/$base_win/openvmm.exe" -f
)
if $copy_remote; then
(
set -x
powershell.exe Copy-Item "$windows_temp_win\\openvmm.exe" "$remote_temp\\openvmm.exe" -Force
)
fi
if $copy_symbols; then
(
set -x
cp -u "$base_win/openvmm.pdb" "$windows_temp/openvmm.pdb" -f
)
fi
echo
if [[ $1 == "run" ]]; then
(
set -x
$openvmm_path $args
)
else
echo $openvmm_path $args
fi
elif [[ $1 == "ohcldiag-dev" ]]; then
shift 2
(
set -x
cargo build --target $arch-pc-windows-msvc -p ohcldiag-dev
cp -u $base_win/ohcldiag-dev.exe "$windows_temp/ohcldiag-dev.exe" -f
"$windows_temp/ohcldiag-dev.exe" "$uhdiag_path" "$@"
)
else
echo "Unknown command: $1"
echo "Usage: $0 <build|run|ohcldiag-dev> <x64|aarch64>..."
exit 1
fi
Testing
This chapter discusses the various kinds of tests you will encounter as an OpenVMM developer.
Unit Tests
Note: We recommend using cargo-nextest to run unit / VMM
tests. It is a significant improvement over the built-in cargo test runner,
and is the test runner we use in all our CI pipelines.
You can install it locally by running: cargo install cargo-nextest --locked
See the cargo-nextest documentation for more info.
Unit tests test individual functions or components without pulling in lots of ambient infrastructure. In Rust, these are usually written in the same file as the product code--this ensures that the test has access to any internal methods or state it requires, and it makes it easier to ensure that tests and code are updated at the same time.
A typical module with unit tests might look something like this:
#![allow(unused)] fn main() { fn add_5(n: u32) -> u32 { n + 5 } #[cfg(test)] mod tests { #[test] fn test_add_5() { assert_eq!(add_5(3), 8); } } }
In the OpenVMM repo, all the unit tests are run on every pull request, on an arbitrary build machine. As a result of this approach, it's important that unit tests:
- run quickly
- do not affect the state of the machine that runs them
- do not take a dependency on machine configuration
- e.g: no root/administrator access or virtualization requirement
We may loosen these guidelines over time if it becomes necessary. You can also
mark tests with #[ignore] if they do not meet these guidelines but are useful
for manual testing.
See the unit testing section in "Rust by example" for more details.
Doc tests
Rust has another type of unit tests known as doc tests. These are unit tests that are written in the API documentation comments of public functions. They will be run automatically along with the unit tests, so the same guidelines apply.
When do you choose a doc test over a unit test?
Doc tests can only access public functionality, and they are intended to document the usage of a function or method, not to exhaustively check every case. So write doc tests primarily as examples for other developers, and rely on unit tests for your main coverage.
An example might look like this:
#![allow(unused)] fn main() { /// Adds 5 to `n`. /// /// ``` /// assert_eq!(mycrate::add_5(3), 8); /// ``` pub fn add_5(n: u32) -> u32 { n + 5 } }
See the documentation testing section in Rust by example for more info.
VMM Tests
The OpenVMM repo contains a set of "heavyweight" VMM tests that fully boot a
virtual machine and run validation against it. Unlike Unit tests, these are all
centralized in a single top-level vmm_tests directory.
The OpenVMM PR and CI pipelines will run the full test suite on all supported platforms; you'd typically run only the tests relevant to the changes you're working on.
Writing VMM Tests
To streamline the process of booting and interacting with VMs during VMM tests, the
OpenVMM project uses an in-house test framework/library called petri.
The library does not yet have a stable API, so at this time, the best way to
learn how to write new VMM tests is by reading through the existing corpus of
tests (start with vmm_tests/vmm_tests/tests/tests/multiarch.rs),
as well as reading through petri's rustdoc-generated API docs.
The tests are currently generated using a macro (#[vmm_test]) that allows
the same test body to be run in a variety of scenarios, with different guest
operating systems, firmwares, and VMMs (including Hyper-V, which is useful
for testing certain OpenHCL features that aren't supported when using
OpenVMM as the host VMM).
"heavy" tests
The global nextest.toml
configures how tests run in our test environments. The default and ci profiles
control things like timeouts, and how many resources we allocate to a given test. The number
of required threads is a fuzzy requirement relative to the number of VPs consumed by the VM under
test, the amount of memory your test needs, the host test framework (petri itself), and so on.
We have some pre-defined overrides that perform filterset matching on test name. These overrides are curated to balance individual trial (test case) performance against overall concurrency on engineers' local machines and in CI. Put these special words in your test to opt in to that override:
heavy- if your test is heavier than the typical vmm_test. E.g., your test explicitly requests 16 virtual processors.very_heavyif your test is heavier than aheavytest. E.g., your test explicitly requests 32 virtual processors.
Running VMM Tests (Flowey)
The easiest way to run the VMM tests locally is using the
cargo xflowey vmm-tests command. To see the most up-to-date options, run:
cargo xflowey vmm-tests --help. When running Hyper-V tests, you will need
to use an administrator terminal window (this works even if you are running
from WSL2). When running Windows tests, the output dir should be on the
Windows file system. For example, from WSL2:
cargo xflowey vmm-tests --target windows-x64 --dir /mnt/e/vmm_tests
This command will build or download all the test dependencies and copy them to a self-contained folder that can be copied to another system for testing. The folder will contain scripts for installing dependencies (install_deps.ps1 on Windows) and running the tests (run.ps1 on Windows). You can either specify a list of flags to disable certain tests and avoid building/downloading some dependencies, or you can specify a custom nextest filter and list of artifacts. In this case, all possible dependencies will be obtained since deriving them from a test filter is not yet supported.
Running VMM Tests (Manual)
Note: We recommend using cargo-nextest to run unit / VMM
tests. It is a significant improvement over the built-in cargo test runner,
and is the test runner we use in all our CI pipelines.
You can install it locally by running: cargo install cargo-nextest --locked
See the cargo-nextest documentation for more info.
You can directly invoke cargo test or cargo nextest to run the vmm
tests manually.
Unlike Unit Tests, VMM tests may rely on additional external artifacts in order to run. e.g: Virtual Disk Images, pre-built OpenHCL binaries, UEFI / PCAT firmware blobs, etc.
As such, the first step in running a VMM test is to ensure you have acquired all external test artifacts it may depend upon.
The VMM test infrastructure does not automatically fetch / rebuild necessary artifacts unless you are using flowey. However, the test infrastructure is designed to report clear and actionable error messages whenever a required test artifact cannot be found, which provide detailed instructions on how to build / acquire the missing artifact. Some dependencies can only be built on Linux (OpenHCL and Linux pipette, for example). If you are building on Linux and want to run Windows guest tests, pipette will need to be cross compiled for Windows.
cargo nextest run won't rebuild any of your changes. Make sure you cargo build
or cargo xflowey igvm [RECIPE] first!
VMM tests are run using standard Rust test infrastructure, and are invoked via
cargo test / cargo nextest.
cargo nextest run -p vmm_tests [TEST_FILTERS]
For example, to run a simple VMM test that simply boots using UEFI:
cargo nextest run -p vmm_tests multiarch::openvmm_uefi_x64_frontpage
And, for further example, to rebuild everything* and run all* the tests (see below for details on these steps):
*This will not work for Hyper-V tests. TMK tests need additional build steps.
# Install (most) of the dependencies; cargo nextest run may tell you
# about other deps.
rustup target add x86_64-unknown-none
rustup target add x86_64-unknown-uefi
rustup target add x86_64-pc-windows-msvc
sudo apt install clang-tools-14 lld-14
cargo install cargo-nextest --locked
cargo xtask guest-test download-image
cargo xtask guest-test uefi --bootx64
# Rebuild all, and run all tests
cargo build --target x86_64-pc-windows-msvc -p pipette
cargo build --target x86_64-unknown-linux-musl -p pipette
cargo build --target x86_64-pc-windows-msvc -p openvmm
cargo xflowey build-igvm x64-test-linux-direct
cargo xflowey build-igvm x64-cvm
cargo xflowey build-igvm x64
cargo nextest run --target x86_64-pc-windows-msvc -p vmm_tests --filter-expr 'all() & !test(hyperv) & !test(tmk)'
[Linux] Cross-compiling pipette.exe
These commands might use the test agent (pipette) that is put inside the VM,
and if the host machine OS and the guest machine OS are different, a setup
is required for cross-building. The recommended approach is to use WSL2 and
cross-compile using the freely available Microsoft Visual Studio Build Tools
or Microsoft Visual Studio Community Edition as described in
[WSL2] Cross Compiling from WSL2 to Windows
If that is not possible, here is another option that relies on MinGW-w64 and doesn't require installing Windows:
# Do 1 once, do 2 as needed.
#
# 1. Setup the toolchain
rustup target add x86_64-pc-windows-gnu
sudo apt-get install mingw-w64-x86-64-dev
mingw-genlib -a x86_64 ./support/pal/api-ms-win-security-base-private-l1-1-1.def
sudo mv libapi-ms-win-security-base-private-l1-1-1.a /usr/x86_64-w64-mingw32/lib
# 2. Build Pipette (builds target/x86_64-pc-windows-gnu/debug/pipette.exe first)
cargo build --target x86_64-pc-windows-gnu -p pipette
# Run a test
cargo nextest run -p vmm_tests multiarch::openvmm_uefi_x64_windows_datacenter_core_2022_x64_boot
Printing logs for VMM Tests
In order to see the OpenVMM logs while running a VMM test, do the following:
- Add the
--no-captureflag to yourcargo nextestcommand. - Set
OPENVMM_LOG=trace, replacingtracewith the log level you want to view.
Azure-hosted Test Images
OpenVMM utilizes pre-made VHDs in order to run tests with multiple guest operating systems. These images are as close to a "stock" installation as possible, created from the Azure Marketplace or downloaded directly from a trusted upstream source.
These VHDs are stored in Azure Blob Storage, and are downloaded when running VMM tests in CI.
Downloading VHDs
The cargo xtask guest-test download-image command can be used to download vhds
to your machine.
By default it will download all available VHDs, however the --vhd option can
be used to only download select guests. After running it the tests can be run
just like any other. This command requires having
AzCopy
installed.
Fuzzing in OpenVMM
Fuzzing infrastructure in OpenVMM is based on the excellent cargo-fuzz project, which makes it super easy to get up-and-running with fuzzing in Rust projects.
For the curious: Under-the-hood, cargo-fuzz hooks into LLVM's
libFuzzer to do the actual fuzzing.
Running Fuzzers Locally
Installing Dependencies
To begin fuzzing in OpenVMM, you'll need to install cargo-fuzz and a nightly
rust compiler.
Installation should be as simple as:
rustup install nightly
cargo install cargo-fuzz
cargo-fuzz requires a nightly toolchain as it compiles targets with
ASAN to
improve the likelihood of finding bugs and the reproducibility of testcases.
Running
While its entirely possible to run the various fuzzers in the OpenVMM repo using
cargo fuzz directly, the OpenVMM repo includes additional tooling to streamline
working with fuzzers at "OpenVMM scale": cargo xtask fuzz
cargo xtask fuzz bridges the gap between cargo fuzz's "crate-oriented"
tooling, and OpenVMM's "repo-oriented" tooling.
e.g: instead of manually navigating to each individual crate/fuzz directory in
order to use cargo fuzz, with cargo xtask fuzz, you can list/run/build any
fuzzer in the OpenVMM repo, regardless where it happens to be in the repo!
Before you can run a fuzzer, you need to know its name. To see a list of all fuzzers currently in the OpenVMM tree, you can run:
cargo xtask fuzz list
The output will be a list of available "fuzz targets":
$ cargo xtask fuzz list
fuzz_chipset_battery
fuzz_ide
fuzz_scsi_buffers
Once you've got a fuzzer you're interested in running (e.g: fuzz_ide),
starting a fuzzing session is as easy as running:
cargo xtask fuzz run fuzz_ide
And you're off! If you see a whole bunch of terminal spew, congrats, you're fuzzing!
When run locally using the above command, the fuzzer will run indefinitely until a crash is discovered.
If you need to tweak the runtime behavior of the command, all of libFuzzer's commandline options are at your disposal. Alternatively you can print the help of the fuzzer like so:
# NOTE: The "-- --" is required to differentiate between `xtask fuzz`'s
# extra-args, and `cargo fuzz`'s extra-args
cargo xtask fuzz run fuzz_ide -- -- -help=1
Other Fuzzing Commands
The cargo xtask fuzz CLI includes plenty of docs via --help text. Don't be
afraid to dig into all the tools available via cargo xtask fuzz by using
--help at both the top-level, and for more details regarding the various
subcommands.
Note that most cargo xtask fuzz commands mirror those from cargo fuzz, so
for additional information on how certain commands work, check out the
cargo-fuzz book.
Coverage
The effectiveness of fuzzing can be measured with code coverage.
Code coverage can be analyzed to determine which branches in the target were exercised and which were missed by the fuzzer. This can be used to determine if the fuzzer needs improvements or is doing an adequate job.
Before you begin you'll need some additional dependencies to generate an html report:
rustup +nightly component add llvm-tools
apt install lcov
To generate a report with "sane defaults", you can simply run:
cargo xtask fuzz coverage fuzz_ide --with-html-report
Simply navigate to the `html/report/dir/index.html`` on your machine and inspect the coverage!
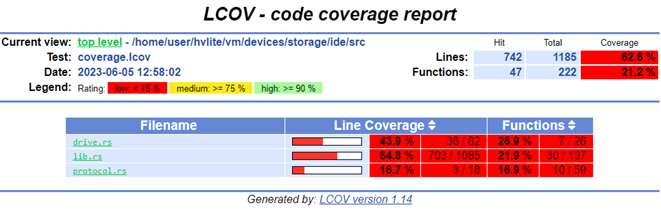
--with-html-report offers a quick-and-easy way for an individual user
generate a coverage report locally, but it may not be entirely appropriate for
more "industrial scale" fuzzing pipelines.
Manual Coverage Generation (Advanced)
The basic way this is done is by running all the discovered input testcases
through the fuzzer and merging all the coverage events together (remember, the
fuzzers only save testcases which generate new coverage). Cargo-fuzz provides a
way to do this with the coverage subcommand. This step generates a
coverage.profdata file which can be turned into a human-readable HTML report:
# cargo xtask fuzz coverage <fuzzer name>
cargo xtask fuzz coverage fuzz_ide
# confirm coverage.profdata was created
ls -l coverage.profdata
OR if you have a large number of inputs (5k+) the below will collect and merge coverage significantly faster:
# rebuild the fuzzer with coverage instrumentation
RUSTFLAGS="-C instrument-coverage" cargo +nightly fuzz build
# set env var to rustup's llvm-preview tools
LLVM_TOOLS_PATH=$(dirname $(find $(rustc +nightly --print sysroot) -name 'llvm-profdata'))
# make an output directory for corups minimation
mkdir min_corp
# run the minimizer putting the raw cov data into coverage.profraw
LLVM_PROFILE_FILE="coverage.profraw" ./fuzz/targets/<target-path>/release/fuzz_ide min_corp <path to input corpus directory> -merge=1
# merge the raw data into coverage.profdata
$LLVM_TOOLS_PATH/llvm-profdata merge -sparse coverage.profraw -o coverage.profdata
Next find the location of the llvm-tools you installed with rustup (NOTE: rustup is used to install the LLVM tools to ensure that rust's llvm version and the tool version are in sync), and convert the coverage data into a report:
# set env var to rustup's llvm-preview tools
LLVM_TOOLS_PATH=$(dirname $(find $(rustc +nightly --print sysroot) -name 'llvm-profdata'))
# covert the coverage data into an lcov format
$LLVM_TOOLS_PATH/llvm-cov export -instr-profile=coverage.profdata \
-format=lcov \
-object ./fuzz/targets/<target-triple>/coverage/<target-triple>/release/fuzz_ide \
--ignore-filename-regex "rustc" > coverage.lcov
# summarize the coverage information
lcov --summary ./coverage.lcov
# make an output directory for the html report
mkdir -p lcov_html
# generate the html report
genhtml -o lcov_html --legend --highlight ./coverage.lcov
Writing Fuzzers
Writing a new fuzzer in OpenVMM
The easiest way to get up and running is to look at the existing in-tree fuzzers
(which you can list using cargo xtask fuzz list), along with reading through
the cargo-fuzz book (the
book is fairly brief and shouldn't take more than 20 minutes to read through)
Some examples of in-tree fuzzers:
- Simple device example: chipset/fuzz/battery.rs
- More complex device example: ide/fuzz/fuzz_ide.rs
- Abstraction over unsafe example: ide/fuzz/fuzz_scsi_buffer.rs
Once you're ready to take a stab at writing your own fuzzer, spinning up a new fuzzer is as easy as running:
cargo xtask fuzz init openvmm_crate_to_fuzz TEMPLATE
Use --help for more details on the available TEMPLATE types.
We don't suggest using cargo fuzz init (i.e: without xtask), as it
emits a template that isn't compatible with the OpenVMM repo style, and also
doesn't properly update the root Cargo.toml's workspace.members array.
Fuzzing an abstraction over unsafe code
Unsafe code is a prioritized target for fuzzing given its self-evident risks.
However, it can be hard to reason about how best to exercise unsafe code in OpenVMM via fuzzing as often (and correctly) the unsafe code is not directly interacting with guest-controlled data.
The approach taken with OpenVMM then is to target abstractions over unsafe code.
Such as interfaces and data structures like BounceBuffers, guest_memory, or
ucs2. A fuzzer for one of these will attempt to be a regular consumer of the
abstraction, calling those APIs declared safe and using any data structure in a
rust-safe way. This attempts to check that the safety guarantees the abstraction
is making are being upheld via the API.
For example, let's say we want to fuzz BounceBuffers, here's what we may
want to fuzz:
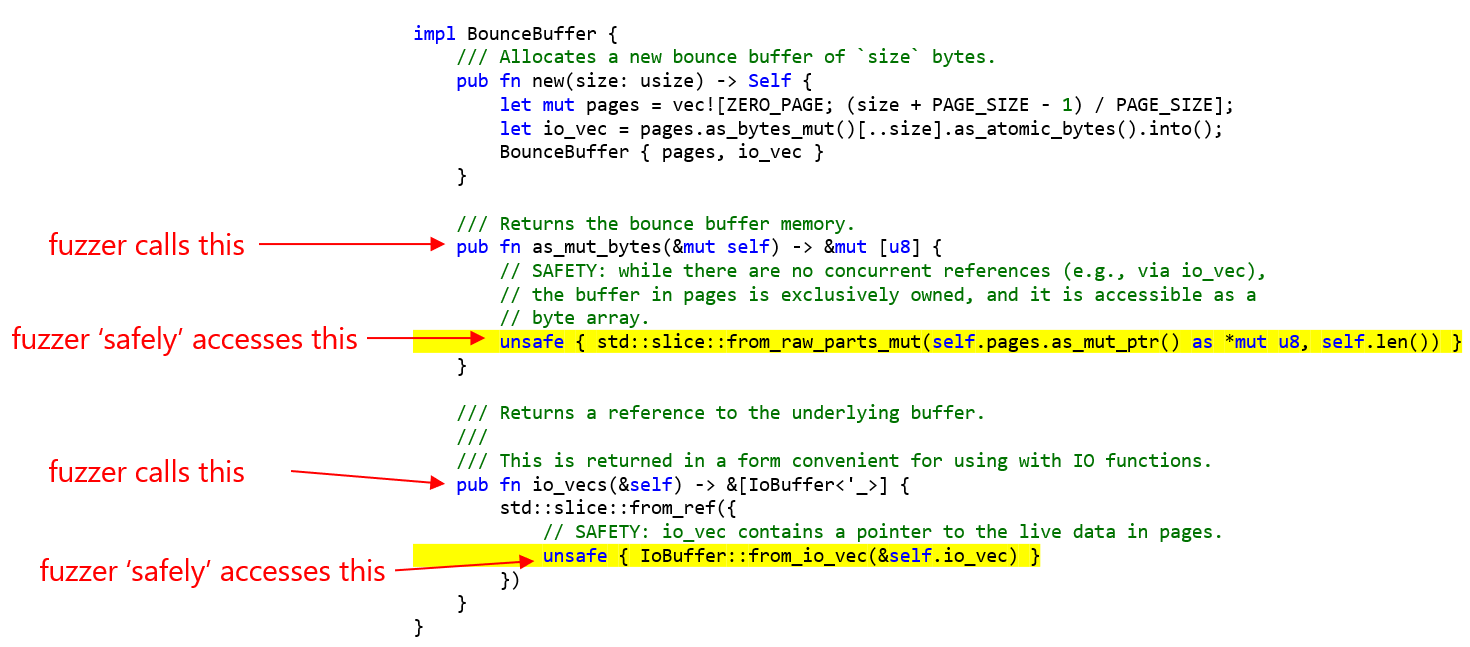
Fuzz logic might then allocate a BounceBuffer using new and call methods on
it such as as_mut_bytes and io_vecs. Then it could access the return result
of both those calls:
use scsi_buffers::BounceBuffer;
#[derive(Arbitrary)]
enum BouneBufferAccess {
AsMutBytes,
IoVecs
}
#[derive(Arbitrary)]
struct FuzzCase {
#[arbitrary(with = |u: &mut Unstructured| u.int_in_range(0..=0x40000))]
size: usize,
accesses: Vec<BounceBufferAccess>
}
fn access_mut_bytes(buf: &mut [u8]) {
buf.fill(b'A');
// access buf in other ways to test validity of underlying memory and slice
}
fn access_io_vecs(io_vecs: &[IoBuffer]) {
// access each IoBuffer to test validity of ptr and len
}
fuzz_target!(|fuzz_case: FuzzCase| { do_fuzz(fuzz_case) });
fn do_fuzz(fuzz_case: FuzzCase) {
let mut bb = BounceBuffer::new(fuzz_case.size);
for access in fuzz_case.accesses {
match access {
AsMutBytes => {
let buf = bb.as_mut_bytes();
access_mut_bytes(buf);
},
IoVecs => {
let io_vecs = bb.io_vecs();
access_io_vecs(io_vecs)
}
}
}
}The fuzzer should work to ensure the safe members of the API cannot be misused in any way that may result in memory corruption or unsoundness.
Fuzzing a chipset device
Writing a fuzzer for a chipset device (e.g: battery, ide, serial, pic, etc...) involves targeting the API that is roughly exposed to guests: the device's port IO, PCI config, and MMIO interfaces.
While it's entirely possible to hand-roll a fuzzer that is tailored to the
specific register configuration of a particular device, the in-repo
chipset_device_fuzz crate exports a FuzzChipset type that offers a
"plug-and-play" way to hook a chipset device up to a fuzzer:
#[derive(Arbitrary)]
struct StaticDeviceConfig {
#[arbitrary(with = |u: &mut Unstructured| u.int_in_range(0..=16))]
num_queues: usize,
}
fn do_fuzz(u: &mut Unstructured<'_>) -> arbitrary::Result<()> {
// Step 1: generate a device's fixed-at-construction-time configuration
let static_device_config: StaticDeviceConfig = u.arbitrary()?;
// Step 2: init the device, and wire-it-up to the fuzz chipset
let mut chipset = chipset_device_fuzz::FuzzChipset::default();
let my_device = chipset.device_builder("my_dev").add(|services| {
my_dev::MyDevice::new(
static_device_config.num_queues,
&mut services.register_mmio(), // e.g: pci devices have BARs to remap their MMIO intercepts
)
}).unwrap();
// Step 3: use the remaining fuzzing input to slam the device with chipset events
while !u.is_empty() {
let action = chipset.get_arbitrary_action(u)?;
xtask_fuzz::fuzz_eprintln!("{:x?}", action); // only prints when running a repro
chipset.exec_action(action).unwrap();
// Step 3.5: (optionally) intersperse "external stimuli" between chipset actions
if u.ratio(1, 10)? {
let event: u32 = u.arbitrary()?;
my_device.report_external_event(event);
}
}
Ok(())
}
fuzz_target!(|input: &[u8]| -> libfuzzer_sys::Corpus {
if do_fuzz(&mut Unstructured::new(input)).is_err() {
libfuzzer_sys::Corpus::Reject
} else {
libfuzzer_sys::Corpus::Keep
}
});Fuzzing a vmbus device
TBD (no such fuzzers exist in-tree today)
Fuzzing async code
Depending on the nature of the 'async' code in question, there are two main recommended approaches to fuzzing it:
-
now_or_never: The recommended approach for individual asynchronous calls is to use the
now_or_nevermethod from thefuturescrate. This method will poll the future to completion, but will not block if the future is not ready to complete. This allows you to fuzz the future without needing to run it to completion, which can be useful for testing the behavior of the future in various states. -
DefaultPool::run_with: The recommended approach for more intricate asynchronous requirements is to use the
DefaultPool::run_withmethod from ourpal_asynccrate. This method takes a custom async function and runs it to completion. This allows you to write custom code using regular async/await syntax, combinators,joins,selects, or whatever you wish.
Dev Tools / Utilities
While most tasks in the OpenVMM repo can be accomplished directly via standard
Rust tooling (i.e: cargo run, cargo build), there are many dev tasks that
don't neatly fall under the cargo umbrella. e.g:
- running code formatters / linters
- orchestrating multi-stage, multi-component OpenHCL builds
- running different kinds of test suites
- building/downloading test images for VMM testing
- setting up git hooks
- etc...
The following chapter discusses some of the various dev-facing tools / utilities you may encounter and/or find useful when working on OpenVMM.
Rust-based Tooling
As with many projects, OpenVMM initially took the simple approach of spinning up ad-hoc Bash/Python scripts, and hand-written YAML workflow automation.
This worked for a while... but as the project continued to grow, our once small and focused set of scripts evolved into a mass of interconnected dependencies, magic strings, and global variables!
To pay down mounting tech debt, and to foster a culture where all devs are empowered to contribute and maintain OpenVMM's project tooling, we have adopted a policy of migrating as much core tooling away from loosely-typed languages (like Bash, Python, and hand-written Workflow YAML), and towards new strongly-typed Rust-based tooling.
Flowey
Flowey is an in-house, Rust library for writing maintainable, cross-platform automation. It enables developers to define CI/CD pipelines and local workflows as type-safe Rust code that can generate backend-specific YAML (Azure DevOps, GitHub Actions) or execute directly on a local machine. Rather than writing automation logic in YAML with implicit dependencies, flowey treats automation as first-class Rust code with explicit, typed dependencies tracked through a directed acyclic graph (DAG).
Why Flowey?
Traditional CI/CD pipelines using YAML-based configuration (e.g., Azure DevOps Pipelines, GitHub Actions workflows) have several fundamental limitations that become increasingly problematic as projects grow in complexity:
The Problems with Traditional YAML Pipelines
Non-Local Reasoning and Global State
- YAML pipelines heavily rely on global state and implicit dependencies (environment variables, file system state, installed tools)
- Understanding what a step does often requires mentally tracking state mutations across the entire pipeline
- Debugging requires reasoning about the entire pipeline context rather than isolated units of work
- Changes in one part of the pipeline can have unexpected effects in distant, seemingly unrelated parts
Maintainability Challenges
- YAML lacks type safety, making it easy to introduce subtle bugs (typos in variable names, incorrect data types, etc.)
- No compile-time validation means errors only surface at runtime
- Refactoring is risky and error-prone without automated tools to catch breaking changes
- Code duplication is common because YAML lacks good abstraction mechanisms
- Testing pipeline logic requires actually running the pipeline, making iteration slow and expensive
Platform Lock-In
- Pipelines are tightly coupled to their specific CI backend (ADO, GitHub Actions, etc.)
- Multi-platform support means maintaining multiple, divergent YAML files
Local Development Gaps
- Developers can't easily test pipeline changes before pushing to CI
- Reproducing CI failures locally is difficult or impossible
- The feedback loop is slow: push → wait for CI → debug → repeat
Flowey's Solution
Flowey addresses these issues by treating automation as first-class Rust code:
- Type Safety: Rust's type system catches errors at compile-time rather than runtime
- Local Reasoning: Dependencies are explicit through typed variables, not implicit through global state
- Portability: Write once, generate YAML for any backend (ADO, GitHub Actions, or run locally)
- Reusability: Nodes are composable building blocks that can be shared across pipelines
Flowey's Directory Structure
Flowey is architected as a standalone tool with a layered crate structure that separates project-agnostic core functionality from project-specific implementations:
flowey_core: Provides the core types and traits shared between user-facing and internal Flowey code, such as the essential abstractions for nodes and pipelines.flowey: Thin wrapper aroundflowey_corethat exposes the public API for defining nodes and pipelines.flowey_cli: Command-line interface for running flowey - handles YAML generation, local execution, and pipeline orchestration.schema_ado_yaml: Rust types for Azure DevOps YAML schemas used during pipeline generation.flowey_lib_common: Ecosystem-wide reusable nodes (installing Rust, running Cargo, downloading tools, etc.) that could be useful across projects outside of OpenVMM.flowey_lib_hvlite: OpenVMM-specific nodes and workflows that build on the common library primitives.flowey_hvlite: The OpenVMM pipeline definitions that compose nodes from the libraries above into complete CI/CD workflows.
Flowey Fundamentals
Before diving into how flowey works, let's establish the key building blocks that form the foundation of flowey's automation model. These concepts are flowey's Rust-based abstractions for common CI/CD workflow primitives.
The Automation Workflow Model
In traditional CI/CD systems, workflows are defined using YAML with implicit dependencies and global state. Flowey takes a fundamentally different approach: automation workflows are modeled as a directed acyclic graph (DAG) of typed, composable Rust components. Each component has explicit inputs and outputs, and dependencies are tracked through the type system.
Core Building Blocks
Flowey's model consists of a hierarchy of components:
Pipelines are the top-level construct that defines a complete automation workflow. A pipeline specifies what work needs to be done and how it should be organized. Pipelines can target different execution backends (local machine, Azure DevOps, GitHub Actions) and generate appropriate configuration for each.
Jobs represent units of work that run on a specific platform (Windows, Linux, macOS) and architecture (x86_64, Aarch64). Jobs can run in parallel when they don't depend on each other, or sequentially when one job's output is needed by another. Each job is isolated and runs in its own environment.
Nodes are reusable units of automation logic that perform specific tasks (e.g., "install Rust toolchain", "run cargo build", "publish test results"). Nodes are invoked by jobs and emit one or more steps to accomplish their purpose. Nodes can depend on other nodes, forming a composable ecosystem of automation building blocks.
Steps are the individual units of work that execute at runtime. A step might run a shell command, execute Rust code, or interact with the CI backend. Steps are emitted by nodes during the build-time phase and executed in dependency order during runtime.
Connecting the Pieces
These building blocks are connected through three key mechanisms:
Variables (ReadVar/WriteVar) enable data flow between steps. A WriteVar<T> represents a promise to produce a value of type T at runtime, while a ReadVar<T> represents a dependency on that value. Variables enforce write-once semantics (each value has exactly one producer) and create explicit dependencies in the DAG. For example, a "build" step might write a binary path to a WriteVar<PathBuf>, and a "test" step would read from the corresponding ReadVar<PathBuf>. This echoes Rust's "shared XOR mutable" ownership rule: a value has either one writer or multiple readers, never both concurrently.
Artifacts enable data transfer between jobs. Since jobs may run on different machines or at different times, artifacts package up files (like compiled binaries, test results, or build outputs) for transfer. Flowey automatically handles uploading artifacts at the end of producing jobs and downloading them at the start of consuming jobs, abstracting away backend-specific artifact APIs.
Side Effects represent dependencies without data. Sometimes step B needs to run after step A, but A doesn't produce any data that B consumes (e.g., "install dependencies" must happen before "run tests", even though the test step doesn't directly use the installation output). Side effects are represented as ReadVar<SideEffect> and establish ordering constraints in the DAG without transferring actual values.
Putting It Together
Here's an example of how these pieces relate:
Pipeline
├─ Job 1 (Linux x86_64)
│ ├─ Node A (install Rust)
│ │ └─ Step: Run rustup install
│ │ └─ Produces: WriteVar<SideEffect> (installation complete)
│ └─ Node B (build project)
│ └─ Step: Run cargo build
│ └─ Consumes: ReadVar<SideEffect> (installation complete)
│ └─ Produces: WriteVar<PathBuf> (binary path) → Artifact
│
└─ Job 2 (Windows x86_64)
└─ Node C (run tests)
└─ Step: Run binary with test inputs
└─ Consumes: ReadVar<PathBuf> (binary path) ← Artifact
└─ Produces: WriteVar<PathBuf> (test results)
In this example:
- The Pipeline defines two jobs that run on different platforms
- Job 1 installs Rust and builds the project, with step dependencies expressed through variables
- Job 2 runs tests using the binary from Job 1, with the binary transferred via an artifact
- Variables create dependencies within a job (build depends on install)
- Artifacts create dependencies between jobs (Job 2 depends on Job 1's output)
- Side Effects represent the "Rust is installed" state without carrying data
Two-Phase Execution Model
Flowey operates in two distinct phases:
-
Build-Time (Resolution Phase): When you run
cargo xflowey regen, flowey:- Reads
.flowey.tomlto determine which pipelines to regenerate - Builds the flowey binary (e.g.,
flowey-hvlite) viacargo build - Runs the flowey binary with
pipeline <backend> --out <file> <cmd>for each pipeline definition - During this invocation, flowey constructs a directed acyclic graph (DAG) by:
- Instantiating all nodes (reusable units of automation logic) defined in the pipeline
- Processing their requests
- Resolving dependencies between nodes via variables and artifacts
- Determining the execution order
- Performing flowey-specific validations (dependency resolution, type checking, etc.)
- Generates YAML files for CI systems (ADO, GitHub Actions) at the paths specified in
.flowey.toml
- Reads
-
Runtime (Execution Phase): The generated YAML is executed by the CI system (or locally via
cargo xflowey <pipeline>). Steps (units of work) run in the order determined at build-time:- Variables are read and written with actual values
- Commands are executed
- Artifacts (data packages passed between jobs) are published/consumed
- Side effects (dependencies) are resolved
The .flowey.toml file at the repo root defines which pipelines to generate and where. For example:
[[pipeline.flowey_hvlite.github]]
file = ".github/workflows/openvmm-pr.yaml"
cmd = ["ci", "checkin-gates", "--config=pr"]
When you run cargo xflowey regen:
- It reads
.flowey.toml - Builds the
flowey-hvlitebinary - Runs
flowey-hvlite pipeline github --out .github/workflows/openvmm-pr.yaml ci checkin-gates --config=pr - This generates/updates the YAML file with the resolved pipeline
Key Distinction:
cargo build -p flowey-hvlite- Only compiles the flowey code to verify it builds successfully. Does not construct the DAG or generate YAML files.cargo xflowey regen- Compiles the code and runs the full build-time resolution to construct the DAG, validate the pipeline, and regenerate all YAML files defined in.flowey.toml.
Always run cargo xflowey regen after modifying pipeline definitions to ensure the generated YAML files reflect your changes.
Backend Abstraction
Flowey supports multiple execution backends:
- Local: Runs directly on your development machine
- ADO (Azure DevOps): Generates ADO Pipeline YAML
- GitHub Actions: Generates GitHub Actions workflow YAML
Nodes should be written to work across ALL backends whenever possible. Relying on ctx.backend() to query the backend or manually emitting backend-specific steps (via emit_ado_step or emit_gh_step) should be avoided unless absolutely necessary. Most automation logic should be backend-agnostic, using emit_rust_step for cross-platform Rust code that works everywhere. Writing cross-platform flowey code enables locally testing pipelines which can be invaluable when iterating over CI changes.
If a node only supports certain backends, it should immediately fast‑fail with a clear error ("<Node> not supported on <backend>") instead of silently proceeding. That failure signals it's time either to add the missing backend support or introduce a multi‑platform abstraction/meta‑node that delegates to platform‑specific nodes.
Steps
Steps are units of work that will be executed at runtime. Different step types exist for different purposes.
Types of Steps
Rust Steps
Rust steps execute Rust code at runtime and are the most common step type in flowey.
emit_rust_step: The primary method for emitting steps that run Rust code. Steps can claim variables, read inputs, perform work, and write outputs. Returns an optional ReadVar<SideEffect> that other steps can use as a dependency.
emit_minor_rust_step: Similar to emit_rust_step but for steps that cannot fail (no Result return) and don't need visibility in CI logs. Used for simple transformations and glue logic. Using minor steps also improve performance, since there is a slight cost to starting and ending a 'step' in GitHub and ADO. During the build stage, minor steps that are adjacent to each other will get merged into one giant CI step.
emit_rust_stepv: Convenience method that combines creating a new variable and emitting a step in one call. The step's return value is automatically written to the new variable.
For detailed examples of Rust steps, see the NodeCtx emit methods documentation.
ADO Steps
emit_ado_step: Emits a step that generates Azure DevOps Pipeline YAML. Takes a closure that returns a YAML string snippet which is interpolated into the generated pipeline.
For ADO step examples, see the NodeCtx::emit_ado_step documentation.
GitHub Steps
emit_gh_step: Creates a GitHub Actions step using the fluent GhStepBuilder API. Supports specifying the action, parameters, outputs, dependencies, and permissions. Returns a builder that must be finalized with .finish(ctx).
For GitHub step examples, see the GhStepBuilder documentation.
Side Effect Steps
emit_side_effect_step: Creates a dependency relationship without executing code. Useful for aggregating multiple side effect dependencies into a single side effect. More efficient than emitting an empty Rust step.
For side effect step examples, see the NodeCtx::emit_side_effect_step documentation.
Isolated Working Directories and Path Immutability
Each step gets its own fresh local working directory. This avoids the "single global working directory dumping ground" common in bash + YAML systems.
However, while flowey variables enforce sharing XOR mutability at the type-system level, developers must manually enforce this at the filesystem level:
Steps must NEVER modify the contents of paths referenced by ReadVar<PathBuf>.
When you write a path to WriteVar<PathBuf>, you're creating an immutable contract. Other steps reading that path must treat it as read-only. If you need to modify files from a ReadVar<PathBuf>, copy them to your step's working directory.
Runtime Services
Runtime services provide the API available during step execution (inside the
closures passed to emit_rust_step, etc.).
RustRuntimeServices
RustRuntimeServices is the primary runtime service available in Rust steps. It provides:
Variable Operations
- Reading and writing flowey variables
- Secret handling (automatic secret propagation for safety)
- Support for reading values of any type that implements
ReadVarValue
Environment Queries
- Backend identification (Local, ADO, or GitHub)
- Platform detection (Windows, Linux, macOS)
- Architecture information (x86_64, Aarch64)
AdoStepServices
AdoStepServices provides integration with Azure DevOps-specific features when emitting ADO YAML steps:
ADO Variable Bridge:
- Convert ADO runtime variables (like
BUILD.SOURCEBRANCH) into flowey vars - Convert flowey vars back into ADO variables for use in YAML
- Handle secret variables appropriately
Repository Resources:
- Resolve repository IDs declared as pipeline resources
- Access repository information in ADO-specific steps
GhStepBuilder
GhStepBuilder is a fluent builder for constructing GitHub Actions steps with:
Step Configuration:
- Specifying the action to use (e.g.,
actions/checkout@v4) - Adding input parameters via
.with() - Capturing step outputs into flowey variables
- Setting conditional execution based on variables
Dependency Management:
- Declaring side-effect dependencies via
.run_after() - Ensuring steps run in the correct order
Permissions:
- Declaring required GITHUB_TOKEN permissions
- Automatic permission aggregation at the job level
Secret Variables and CI Backend Integration
Flowey provides built-in support for handling sensitive data like API keys, tokens, and credentials through secret variables. Secret variables are treated specially to prevent accidental exposure in logs and CI outputs.
How Secret Handling Works
When a variable is marked as secret, flowey ensures:
- The value is not logged or printed in step output
- CI backends (ADO, GitHub Actions) are instructed to mask the value in their logs
- Secret status is automatically propagated to prevent leaks
Automatic Secret Propagation
To prevent accidental leaks, flowey uses conservative automatic secret propagation:
If a step reads a secret value, all subsequent writes from that step are automatically marked as secret by default. This prevents accidentally leaking secrets through derived values.
For example:
#![allow(unused)] fn main() { ctx.emit_rust_step("process token", |ctx| { let secret_token = secret_token.claim(ctx); let output_var = output_var.claim(ctx); |rt| { let token = rt.read(secret_token); // Reading a secret // This write is AUTOMATICALLY marked as secret // (even though we're just writing "done") rt.write(output_var, &"done".to_string()); Ok(()) } }); }
If you need to write non-secret data after reading a secret, use write_not_secret():
#![allow(unused)] fn main() { rt.write_not_secret(output_var, &"done".to_string()); }
Best Practices for Secrets
- Never use
ReadVar::from_static()for secrets - static values are encoded in plain text in the generated YAML - Always use
write_secret()when writing sensitive data like tokens, passwords, or keys - Minimize secret lifetime - read secrets as late as possible and don't pass them through more variables than necessary
Variables
Variables are flowey's mechanism for creating typed data dependencies between steps. When a node emits steps, it uses ReadVar<T> and WriteVar<T> to declare what data each step consumes and produces. This creates explicit edges in the dependency graph: if step B reads from a variable that step A writes to, flowey ensures step A executes before step B.
Claiming Variables
Before a step can use a ReadVar or WriteVar, it must claim it. Claiming serves several purposes:
- Registers that this step depends on (or produces) this variable
- Converts
ReadVar<T, VarNotClaimed>toReadVar<T, VarClaimed> - Allows flowey to track variable usage for graph construction
Variables can only be claimed inside step closures using the claim() method.
Nested closure pattern and related contexts:
#![allow(unused)] fn main() { // Inside a SimpleFlowNode's process_request() method fn process_request(&self, request: Self::Request, ctx: &mut NodeCtx<'_>) { // Assume a single Request provided an input ReadVar and output WriteVar let input_var: ReadVar<String> = /* from one of the requests */; let output_var: WriteVar<i32> = /* from one of the requests */; // Declare a step (still build-time). This adds a node to the DAG. ctx.emit_rust_step("compute length", |step| { // step : StepCtx (outer closure, build-time) // Claim dependencies so the graph knows: this step READS input_var, WRITES output_var. let input_var = input_var.claim(step); let output_var = output_var.claim(step); // Return the runtime closure. move |rt| { // rt : RustRuntimeServices (runtime phase) let input = rt.read(input_var); // consume value let len = input.len() as i32; rt.write(output_var, &len); // fulfill promise Ok(()) } }); } }
Why the nested closure dance?
The nested closure pattern is fundamental to flowey's two-phase execution model:
- Build-Time (Outer Closure): When flowey constructs the DAG, the outer closure runs to:
- Claim variables, which registers dependencies in the graph
- Determine what this step depends on (reads) and produces (writes)
- Allow flowey determine execution order
- Returns an inner closure that gets invoked during the job's runtime
- Runtime (Inner Closure): When the pipeline actually executes, the inner closure runs to:
- Read actual values from claimed
ReadVars - Perform the real work (computations, running commands, etc.)
- Write actual values to claimed
WriteVars
- Read actual values from claimed
-
NodeCtx: Used when emitting steps (during the build-time phase). Providesemit_*methods,new_var(),req(), etc. -
StepCtx: Used inside step closures (during runtime execution). Provides access toclaim()for variables, and basic environment info (backend(),platform()).
The type system enforces this separation: claim() requires StepCtx (only available in the outer closure), while read()/write() require RustRuntimeServices (only available in the inner closure).
ClaimedReadVar and ClaimedWriteVar
These are type aliases for claimed variables:
ClaimedReadVar<T>=ReadVar<T, VarClaimed>ClaimedWriteVar<T>=WriteVar<T, VarClaimed>
Only claimed variables can be read/written at runtime.
Implementation Detail: Zero-Sized Types (ZSTs)
The claim state markers VarClaimed and VarNotClaimed are zero-sized types (ZSTs) - they exist purely at the type level. It allows Rust to statically verify that all variables used in a runtime block have been claimed by that block.
The type system ensures that claim() is the only way to convert from VarNotClaimed to VarClaimed, and this conversion can only happen within the outer closure where StepCtx is available.
Static Values vs Runtime Values
Sometimes you know a value at build-time:
#![allow(unused)] fn main() { // Create a ReadVar with a static value let version = ReadVar::from_static("1.2.3".to_string()); // This is encoded directly in the pipeline, not computed at runtime // WARNING: Never use this for secrets! }
This can be used as an escape hatch when you have a Request (that expects a value to be determined at runtime), but in a given instance you know the value at build-time.
Variable Operations
ReadVar provides operations for transforming and combining variables:
map(): Transform aReadVar<T>into aReadVar<U>zip(): Combine two ReadVars intoReadVar<(T, U)>into_side_effect(): ConvertReadVar<T>toReadVar<SideEffect>when you only care about ordering, not the valuedepending_on(): Create a new ReadVar with an explicit dependency
For detailed examples, see the ReadVar documentation.
Nodes
At a conceptual level, a Flowey node is analogous to a strongly typed function: you "invoke" it by submitting one or more Request values (its parameters), and it responds by emitting steps that perform work and produce outputs (values written to WriteVars, published artifacts, or side-effect dependencies).
The Node/Request Pattern
Every node has an associated Request type that defines what operations the node can perform. Requests are defined using the flowey_request! macro and registered with new_flow_node! or new_simple_flow_node! macros.
For complete examples, see the FlowNode trait documentation.
FlowNode vs SimpleFlowNode
Flowey provides two node implementation patterns with a fundamental difference in their Request structure and complexity:
SimpleFlowNode - for straightforward, function-like operations:
- Uses a single struct Request type
- Processes one request at a time independently
- Behaves like a "plain old function" that resolves its single request type
- Each invocation is isolated - no shared state or coordination between requests
- Simpler implementation with less boilerplate
- Ideal for straightforward operations like running a command or transforming data
Example use case: A node that runs cargo build - each request is independent and just needs to know what to build.
FlowNode - for complex nodes requiring coordination and non-local configuration:
- Often uses an enum Request with multiple variants
- Receives all requests as a
Vec<Request>and processes them together - Can aggregate, optimize, and consolidate multiple requests into fewer steps
- Enables non-local configuration - critical for simplifying complex pipelines
The Non-Local Configuration Pattern
The key advantage of FlowNode is its ability to accept configuration from different parts of the node graph without forcing intermediate nodes to be aware of that configuration. This is the "non-local" aspect:
Consider an "install Rust toolchain" node with an enum Request:
#![allow(unused)] fn main() { enum Request { SetVersion { version: String }, GetToolchain { toolchain_path: WriteVar<PathBuf> }, } }
Without this pattern (struct-only requests), you'd need to thread the Rust version through every intermediate node in the call graph:
Root Node (knows version: "1.75")
→ Node A (must pass through version)
→ Node B (must pass through version)
→ Node C (must pass through version)
→ Install Rust Node (finally uses version)
With FlowNode's enum Request, the root node can send Request::SetVersion once, while intermediate nodes that don't care about the version can simply send Request::GetToolchain:
Root Node → InstallRust::SetVersion("1.75")
→ Node A
→ Node B
→ Node C → InstallRust::GetToolchain()
The Install Rust FlowNode receives both requests together, validates that exactly one SetVersion was provided, and fulfills all the GetToolchain requests with that configured version. The intermediate nodes (A, B, C) never needed to know about or pass through version information.
This pattern:
- Eliminates plumbing complexity in large pipelines
- Allows global configuration to be set once at the top level
- Keeps unrelated nodes decoupled from configuration they don't need
- Enables validation that required configuration was provided (exactly one
SetVersion)
Additional Benefits of FlowNode:
- Optimize and consolidate multiple similar requests into fewer steps (e.g., installing a tool once for many consumers)
- Resolve conflicts or enforce consistency across requests
For detailed comparisons and examples, see the FlowNode and SimpleFlowNode documentation.
Node Registration
Nodes are automatically registered using macros that handle most of the boilerplate:
new_flow_node!(struct Node)- registers a FlowNodenew_simple_flow_node!(struct Node)- registers a SimpleFlowNodeflowey_request!- defines the Request type and implementsIntoRequest
The imports() Method
The imports() method declares which other nodes this node might depend on. This enables flowey to:
- Validate that all dependencies are available
- Build the complete dependency graph
- Catch missing dependencies at build-time
Why declare imports? Flowey needs to know the full set of potentially-used nodes at compilation time to properly resolve the dependency graph.
For more on node imports, see the FlowNode::imports documentation.
The emit() Method
The emit() method is where a node's actual logic lives. For FlowNode, it receives all requests together and must:
- Aggregate and validate requests (ensuring consistency where needed)
- Emit steps to perform the work
- Wire up dependencies between steps via variables
For SimpleFlowNode, the equivalent process_request() method processes one request at a time.
For complete implementation examples, see the FlowNode::emit documentation.
Node Design Philosophy
Flowey nodes are designed around several key principles:
1. Composability
Nodes should be reusable building blocks that can be combined to build complex workflows. Each node should have a single, well-defined responsibility.
❌ Bad: A node that "builds and tests the project"
✅ Good: Separate nodes for "build project" and "run tests"
2. Explicit Dependencies
Dependencies between steps should be explicit through variables, not implicit through side effects.
❌ Bad: Assuming a tool is already installed
✅ Good: Taking a ReadVar<SideEffect> that proves installation happened
3. Backend Abstraction
Nodes should work across all backends when possible. Backend-specific behavior should be isolated and documented.
4. Separation of Concerns
Keep node definition (request types, dependencies) separate from step implementation (runtime logic):
- Node definition: What the node does, what it depends on
- Step implementation: How it does it
Common Patterns
Request Aggregation and Validation
When a FlowNode receives multiple requests, it often needs to ensure certain values are consistent across all requests while collecting others. The same_across_all_reqs helper function simplifies this pattern by validating that a value is identical across all requests.
Key concepts:
- Iterate through all requests and separate them by type
- Use
same_across_all_reqsto validate values that must be consistent - Collect values that can have multiple instances (like output variables)
- Validate that required values were provided
For a complete example, see the same_across_all_reqs documentation.
Conditional Execution Based on Backend/Platform
Nodes can query the current backend and platform to emit platform-specific or backend-specific steps. This allows nodes to adapt their behavior based on the execution environment.
Key concepts:
- Use
ctx.backend()to check if running locally, on ADO, or on GitHub Actions - Use
ctx.platform()to check the operating system (Windows, Linux, macOS) - Use
ctx.arch()to check the architecture (x86_64, Aarch64) - Emit different steps or use different tool configurations based on these values
When to use:
- Installing platform-specific tools or dependencies
- Using different commands on Windows vs Unix systems
- Optimizing for local development vs CI environments
For more on backend and platform APIs, see the NodeCtx documentation.
Artifacts
Artifacts enable typed data transfer between jobs with automatic dependency management, abstracting away CI system complexities like name collisions and manual job ordering.
Typed vs Untyped Artifacts
Typed artifacts (recommended) provide type-safe artifact handling by defining
a custom type that implements the Artifact trait:
#![allow(unused)] fn main() { #[derive(Serialize, Deserialize)] struct MyArtifact { #[serde(rename = "output.bin")] binary: PathBuf, #[serde(rename = "metadata.json")] metadata: PathBuf, } impl Artifact for MyArtifact {} let (pub_artifact, use_artifact) = pipeline.new_typed_artifact("my-files"); }
Untyped artifacts provide simple directory-based artifacts for simpler cases:
#![allow(unused)] fn main() { let (pub_artifact, use_artifact) = pipeline.new_artifact("my-files"); }
For detailed examples of defining and using artifacts, see the Artifact trait documentation.
Both pipeline.new_typed_artifact("name") and pipeline.new_artifact("name") return a tuple of handles: (pub_artifact, use_artifact). When defining a job you convert them with the job context:
#![allow(unused)] fn main() { // In a producing job: let artifact_out = ctx.publish_artifact(pub_artifact); // artifact_out : WriteVar<MyArtifact> (typed) // or WriteVar<PathBuf> for untyped // In a consuming job: let artifact_in = ctx.use_artifact(use_artifact); // artifact_in : ReadVar<MyArtifact> (typed) // or ReadVar<PathBuf> for untyped }
After conversion, you treat the returned WriteVar / ReadVar like any other flowey variable (claim them in steps, write/read values).
Key concepts:
- The
Artifacttrait works by serializing your type to JSON in a format that reflects a directory structure - Use
#[serde(rename = "file.exe")]to specify exact file names - Typed artifacts ensure compile-time type safety when passing data between jobs
- Untyped artifacts are simpler but don't provide type guarantees
- Tuple handles must be lifted with
ctx.publish_artifact(...)/ctx.use_artifact(...)to become flowey variables
How Flowey Manages Artifacts Under the Hood
During the pipeline resolution phase (build-time), flowey:
- Identifies artifact producers and consumers by analyzing which jobs write to vs read from each artifact's
WriteVar/ReadVar - Constructs the job dependency graph ensuring producers run before consumers
- Generates backend-specific upload/download steps in the appropriate places:
- For ADO: Uses
PublishPipelineArtifactandDownloadPipelineArtifacttasks - For GitHub Actions: Uses
actions/upload-artifactandactions/download-artifact - For local execution: Uses filesystem copying
- For ADO: Uses
At runtime, the artifact ReadVar<PathBuf> and WriteVar<PathBuf> work just like any other flowey variable:
- Producing jobs write artifact files to the path from
WriteVar<PathBuf> - Flowey automatically uploads those files as an artifact
- Consuming jobs read the path from
ReadVar<PathBuf>where flowey has downloaded the artifact
Pipelines
Pipelines define complete automation workflows consisting of jobs that run nodes. See the IntoPipeline trait documentation for detailed examples.
Pipeline Jobs
PipelineJob instances are configured using a builder pattern:
#![allow(unused)] fn main() { let job = pipeline .new_job(platform, arch, "my-job") .with_timeout_in_minutes(60) .with_condition(some_param) .ado_set_pool("my-pool") .gh_set_pool(GhRunner::UbuntuLatest) .dep_on(|ctx| { // Define what nodes this job depends on some_node::Request { /* ... */ } }) .finish(); }
Pipeline Parameters
Parameters allow runtime configuration of pipelines. In Azure DevOps, parameters appear as editable fields in the Run pipeline UI (name, description, default).

#![allow(unused)] fn main() { // Define a boolean parameter let verbose = pipeline.new_parameter_bool( "verbose", "Run with verbose output", ParameterKind::Stable, Some(false) // default value ); // Use the parameter in a job let job = pipeline.new_job(...) .dep_on(|ctx| { let verbose = ctx.use_parameter(verbose); // verbose is now a ReadVar<bool> }) .finish(); }
Stable vs Unstable Parameters
Every parameter in flowey must be declared as either Stable or Unstable using ParameterKind. This classification determines the parameter's visibility and API stability:
Stable Parameters (ParameterKind::Stable)
Stable parameters represent a public, stable API for the pipeline:
- External Visibility: The parameter name is exposed as-is in the generated CI YAML, making it callable by external pipelines and users.
- API Contract: Once a parameter is marked stable, its name and behavior should be maintained for backward compatibility. Removing or renaming a stable parameter is a breaking change.
- Use Cases:
- Parameters that control major pipeline behavior (e.g.,
enable_tests,build_configuration) - Parameters intended for use by other teams or external automation
- Parameters documented as part of the pipeline's public interface
- Parameters that control major pipeline behavior (e.g.,
Unstable Parameters (ParameterKind::Unstable)
Unstable parameters are for internal use and experimentation:
- Internal Only: The parameter name is prefixed with
__unstable_in the generated YAML (e.g.,__unstable_debug_mode), signaling that it's not part of the stable API. - No Stability Guarantee: Unstable parameters can be renamed, removed, or have their behavior changed without notice. External consumers should not depend on them.
- Use Cases:
- Experimental features or debugging flags
- Internal pipeline configuration that may change frequently
- Parameters for development/testing that shouldn't be used in production
cargo xtask
cargo xtask is OpenVMM's "swiss army knife" Rust binary that houses various
bits of project specific tooling.
For more info on how xtask is different from xflowey, see xflowey vs
xtask.
Some examples of tools that you can find under xtask:
cargo xtask fmtimplements various OpenVMM-specific style / linting rulescargo xtask fuzzimplements various OpenVMM-specificcargo fuzzextensionscargo xtask install-git-hookssets up git hooks for developers
This list is not exhaustive. Running cargo xtask will list what tools are
available, along with brief descriptions of what they do / how to use them.
For more information of the xtask pattern, see https://github.com/matklad/cargo-xtask
cargo xflowey
To implement various developer workflows (both locally, as well as in CI), the
OpenVMM project relies on flowey: a custom, in-house Rust library/framework
for writing maintainable, cross-platform automation.
cargo xflowey is a cargo alias that makes it easy for developers to run
flowey-based pipelines locally.
Some particularly notable pipelines:
cargo xflowey build-igvm- primarily dev-tool used to build OpenHCL IGVM files locallycargo xflowey restore-packages- restores external packages needed to compile and run OpenVMM / OpenHCL
xflowey vs xtask
In a nutshell:
cargo xtask: implements novel, standalone tools/utilitiescargo xflowey: orchestrates invoking a sequence of tools/utilities, without doing any non-trivial data processing itself
VmgsTool
OpenHCL VMs store their firmware state and attributes (UEFI variables) in a special VM Guest State (VMGS) file. The OpenHCL interacts with and persists data in the VMGS file on behalf of the VM. The VMGS file is packaged as a VHD which the host OS interacts with. For Confidential OpenHCL VMs, this VHD can be encrypted before VM deployment, so that the host only interacts with an encrypted VHD and hence the file's contents are kept confidential from the host.
The VMGS file contains several elements called "files" (these are not strictly files, simply "chunks of data”, logical groupings of data). Each "file" has a unique, well known index; for example, vTPM state is stored in file id "3".
The VmgsTool is a tool that allows for offline manipulation of a VMGS (version 3) file for provisioning and debugging purposes. Basically, it's a tool to interact with the VMGS file, and it can help you perform operations such as reading, creating, modifying and removing "files" from the VMGS file and even creating an encrypted datastore to allow certain "files" to be encrypted as the scenario requires it.
Alternatively: Pre-Built Binaries
If you would prefer to use VmgsTool without building it from scratch, you can download pre-built copies of the binary from OpenVMM CI.
Simply select a successful pipeline run (should have a Green checkbox), and
scroll down to select an appropriate *-vmgstool artifact for your particular
architecture and operating system.
Running
Note: The examples in this section use the Windows executable vmgstool.exe,
which can be replaced with the Linux executable vmgstool.
Developers who have already setup their development environment may also use
the appropriate cargo run command. For more details on building,
see the build section below.
The VmgsTool commands are always evolving, so use vmgstool.exe --help to see the
most up to date information about the available commands. Options for each command
and subcommand are also available. For example: vmgstool.exe uefi-nvram dump --help
Read and Write Raw Data
To read raw data from a VMGS file, use the dump command. For example, to
export the decrypted binary contents of the BIOS_NVRAM (--fileid 1) to a file:
vmgstool.exe dump --filepath <vmgs file path> --keypath <key file path> --datapath <data file path> --fileid 1
To write raw data to a VMGS file, use the write command. For example, to write
those NVRAM variables to a different, unencrypted VMGS file:
vmgstool.exe write --filepath <vmgs file path> --datapath <data file path> --fileid 1
Read and Parse UEFI NVRAM Variables
Furthermore, the VmgsTool contains parsers to help debug issues with the UEFI NVRAM variables stored in the VMGS FileId 1 (BIOS_NVRAM). For example, to dump the NVRAM variables for an encrypted VMGS file, truncating the binary data contents of variables without parsers:
vmgstool.exe uefi-nvram dump --filepath <vmgs file path> --keypath <key file path> --truncate
Delete Boot Variables to Recover a VM that Fails to Boot
A VM may fail to boot if the disk configuration changes and
UEFI's DefaultBootAlwaysAttempt setting is disabled.
Deleting the existing (invalid) boot entries using VmgsTool
will trigger a default boot (which attempts to boot all available partitions and devices).
To print the boot entries in an encrypted VMGS file:
vmgstool.exe uefi-nvram remove-boot-entries --filepath <vmgs file path> --keypath <key file path> --dry-run
To actually remove the boot entries from the VMGS file, remove --dry-run.
This will remove all Boot#### variables and the BootOrder variable.
If you would like to remove a specific boot entry or any other UEFI NVRAM variable,
use remove-entry. For example, to remove Boot0000:
vmgstool.exe uefi-nvram remove-entry --filepath <vmgs file path>--keypath <key file path> --name Boot0000 --vendor 8be4df61-93ca-11d2-aa0d-00e098032b8c
Troubleshooting
Expected at least N more bytes, but only found M
If you get an error similar to the one below, it is likely that you are trying to read an encrypted VMGS file and haven't provided the correct decryption key.
ERROR: remove_boot_entries error
Caused by:
0: error loading data from Nvram storage
1: unexpected EOF. expected at least 2330702412 more bytes, but only found 30067
Building
Prior to building VmgsTool, please ensure you have built either OpenVMM or OpenHCL at least once, to ensure you have all necessary build dependencies installed.
VmgsTool can be built with cargo build -p vmgstool for Windows and Linux.
To interact with encrypted VMGS files, you will need to compile with the
appropriate encryption feature.
Windows: cargo build --features "encryption_win" -p vmgstool
Linux/WSL2: cargo build --features "encryption_ossl" -p vmgstool
guest_test_uefi
guest_test_uefi is a minimal no_std + alloc EFI application which hosts
a variety of OpenVMM-specific "bare metal" unit tests.
Want to write to an arbitrary MMIO/PIO address? Go for it! It's just you, the VM, and the (very unobtrusive) UEFI runtime!
Building + Running
guest_test_uefi must be built for *-unknown-uefi targets. These are not
installed by default, so you'll need to install the correct target via rustup.
For example:
rustup target add x86_64-unknown-uefi
Since this code runs in the guest, the built .efi binary needs to get packaged
into a disk image that UEFI can read.
To streamline the process of obtaining such a disk image, cargo xtask includes
a helper to generate properly formatted .img files containing a given .efi
image. e.g:
# build the UEFI test application
cargo build -p guest_test_uefi --target x86_64-unknown-uefi
# create the disk image
cargo xtask guest-test uefi --bootx64 ./target/x86_64-unknown-uefi/debug/guest_test_uefi.efi
# test in OpenVMM
cargo run -- --uefi --gfx --hv --processors 1 --disk memdiff:./target/x86_64-unknown-uefi/debug/guest_test_uefi.img
Protip: this is a generic UEFI binary, and can be run outside of the OpenVMM repo as well (e.g: in QEMU, Hyper-V, etc...)!
To convert the raw .img into other formats, qemu-img is very helpful:
# Adjust for the target architecture and type of the build
OVMM_UEFI_TEST_IMG_DIR=./target/x86_64-unknown-uefi/debug
# VmWare
qemu-img convert -f raw -O vmdk ${OVMM_UEFI_TEST_IMG_DIR}/guest_test_uefi.img ${OVMM_UEFI_TEST_IMG_DIR}/guest_test_uefi.vmdk
# Hyper-V
qemu-img convert -f raw -O vhdx ${OVMM_UEFI_TEST_IMG_DIR}/guest_test_uefi.img ${OVMM_UEFI_TEST_IMG_DIR}/guest_test_uefi.vhdx
# The files:
ls -la $OVMM_UEFI_TEST_IMG_DIR/{*.img,*.vhdx,*.vmdk}
hypestv
hypestv is an interactive command-line interface for Hyper-V VMs, designed for
making OpenHCL developers' lives easier.
Similar to ohcldiag-dev, it can interact with the OpenHCL paravisor
running inside a Hyper-V VM. But unlike ohcldiag-dev, it sports an interactive
terminal interface (with history and tab completion), and it is specifically
designed to interact with Hyper-VMs.
In many ways, it is similar to the OpenVMM interactive console. In time, it may
end up sharing code and capabilities with it and with ohcldiag-dev, but it
will always be a Hyper-V specific tool.
Currently, it can:
- Change VM state (starting/stopping/resetting)
- Enable serial port output to standard output, or input/output to another terminal window
- Enable paravisor log output to standard output or another terminal window
- Inspect paravisor state
- Modify the paravisor (update the paravisor command line, reload the paravisor)
In the future, it might be able to:
- Enable Hyper-V log output
- Capture serial port output to a file
- Inspect host state
- Persistence workspaces (save/restore configured serial ports and logs)
Example session
hypestv launches into a detached mode, unless you specify a VM name on the
command line. To select a VM to work on, the VM named tdxvm in this example,
use the select command. If successful, you will now see the name and VM state
in the prompt:
> select tdxvm
tdxvm [off]>
After this, all commands will implicitly operate on tdxvm. Use select again
to work on another VM.
To enable serial port output, use the serial command. This can be used at any
time, even while the VM is not running. E.g., to open a separate window for
interactive use of COM1 and enable logging serial port output for COM2:
tdxvm [off]> serial 1 term
tdxvm [off]> serial 2 log
You can also enable paravisor log output at any time:
tdxvm [off]> paravisor kmsg log
Start a VM with start. This is an asynchronous command: you can continue to
type other commands at the prompt while the VM starts. You should see an output
message when the VM finishes starting, as well as output about any configured
serial ports connecting.
Note that, due to limitations of the rustyline crate, the displayed VM state
on the prompt may not be accurate until you type another command or press Enter.
tdxvm [off]> start
com1 connected
com2 connected
VM started
tdxvm [off]>
tdxvm [running]>
At this point, the VM is running, including the paravisor (if one is
configured). As in the OpenVMM interactive console, you can inspect paravisor
state with the inspect or x command, but under the paravisor/pv command:
tdxvm [running]> pv x
{
build_info: _,
control_state: "started",
mesh: _,
proc: _,
trace: _,
uhdiag: _,
vm: _,
}
You can terminate the VM with kill. This will disconnect any connected serial
ports as well, but they will reconnect next time the VM starts. Killing a VM
does not detach/deselect it; subsequent commands will continue to operate on the
VM.
tdxvm [running]> kill
com1 disconnected
com2 disconnected
VM killed
tdxvm [stopping]>
tdxvm [off]>
Contributing
This chapter discusses various things developers should be aware of prior to submitting changes to the OpenVMM project.
This includes both code-level coding conventions, as well as instructions on properly submitting changes to the OpenVMM GitHub repo, and expectations around code reviews.
Coding conventions
One of our major goals with OpenVMM is to provide a high quality coding experience for contributors, starting first-and-foremost by having a consistent set of coding conventions in the project.
Do your part and keep OpenVMM clean!
rustfmt
Checked Automatically: Yes (via cargo xtask fmt rustfmt)
OpenVMM source must be formatted using rustfmt, which automatically and mechanically applies standard formatting to all the code. This eliminates time spent discussing or reviewing stylistic issues in pull requests.
The CI will run rustfmt --check to enforce consistent formatting, and will
fail if it notices any discrepancies.
Unfortunately, rustfmt isn't infinitely customizable, and there are several
rules that are must be manually enforced:
- All lines must end with LF, not CRLF.
- Top-level
useimports should be non-nested.
Some of these manually-enforced conventions were introduced late into OpenVMM's development, and there may be chunks of the codebase that do not adhere to these conventions.
If you're working in a file and notice that it isn't following a certain convention, please take a moment to fix it!
Assuming you've followed the suggested dev env setup
and set up rust-analyzer to format-on-save, you should rarely have to think
about formatting in .rs files.
House Rules
Checked Automatically: Yes (via cargo xtask fmt house-rules)
"House-rules" are a set of misc code lints that are specific to OpenVMM, which are enforced using a custom in-house tool:
- enforce the presence of the standard Microsoft copyright header
- enforce in-repo crate names don't use '-' in their name (use '_' instead)
- enforce Cargo.toml files don't include autogenerated "see more keys" comments
- enforce Cargo.toml files don't contain author or version fields
- enforce files end with a single trailing newline
- deny usage of
#[repr(packed)](you want#[repr(C, packed)]) - justify usage of
cfg(target_arch = ...)(useguest_archinstead!) - justify usage of
expect(unsafe_code)with an UNSAFETY comment
Some of these lints are self explanatory, whereas others are described in more detail elsewhere on this page.
Unused Cargo.toml Dependencies
Checked Automatically: Yes (via cargo xtask fmt unused-deps)
We have an in-repo fork of
cargo-machete that ensures
Cargo.toml files only include dependencies that are actually being used.
Avoiding unused dependencies makes it easier to reason about what a crate is doing just by looking at its dependencies, and also helps cut-down on incremental compile times.
Formatting (Cargo.toml)
Checked Automatically: No
When defining dependencies in Cargo.toml files, please organize dependencies
into the following groups:
- crate-specific "subcrates"
- crates under vm/
- crates under vm/vmcore/
- crates under support/
- external dependencies
The rationale here is that crates should be grouped according to how related to how widely applicable they are. i.e: crates from crates.io and support are widely applicable outside of OpenVMM, whereas crates under vmcore/ only make sense within the context of OpenVMM, and crate-specific subcrates are - by definition - only applicable to the crate they are being imported from.
Additionally, we make use of the
workspace dependencies
feature to ensure that all our dependencies stay in sync. This requires defining
dependencies in your crate's Cargo.toml file and in the project's root Cargo.toml.
So, for example:
[package]
name = "openvmm"
[dependencies]
# crate-specific subcrates
openvmm_core.workspace = true
...
# /vmcore
vmcore.workspace = true
...
# /vm/devices
firmware_uefi_custom_vars.workspace = true
storvsp.workspace = true
...
# /support
guid.workspace = true
inspect.workspace = true
inspect_proto.workspace = true
...
# external dependencies
anyhow.workspace = true
cfg-if.workspace = true
clap.workspace = true
...
Linting (via clippy)
Checked Automatically: Yes
OpenVMM uses cargo clippy to
supplement rustc's built-in lints.
Assuming you've followed the guide and set up rust-analyzer to
use clippy, you should see clippy lints
appear inline when working on Rust code.
The CI runs cargo clippy on every crate in the repo prior to building the
project, and will fast-fail if it catches any warnings / errors.
Suppressing Lints
In general, lints should be fixed by modifying the code to satisfy the lint.
However, there are cases where a lint may need to be expect'd inline.
In these cases, you must provide a inline comment providing reasonable justification for the suppressed lint.
e.g:
// x86_64-unknown-linux-musl targets have a different type defn for
// `libc::cmsghdr`, hence why these lints are being suppressed.
#[expect(clippy::needless_update, clippy::useless_conversion)]
libc::cmsghdr {
cmsg_level: libc::SOL_SOCKET,
cmsg_type: libc::SCM_RIGHTS,
cmsg_len: (size_of::<libc::cmsghdr>() + size_of_val(fds))
.try_into()
.unwrap(),
..std::mem::zeroed()
}OpenVMM's clippy Configuration
We stick fairly close to the default set of rustc / clippy lints, though there are some default lints that we've decided to disabled project wide, and other non-default lints which we've explicitly opted into.
See the [workspace.lints] sections of OpenVMM's root
Cargo.toml
for a list of globally enabled/disabled lints, along with justification as to
why certain lints have been enabled/disabled.
Unsafe Code Policy
When possible, try to avoid introducing new unsafe code!
Before rolling your own unsafe code, check to see if a safe abstraction
already exists, either in-tree, on crates.io*, or in the standard library.
*subject to an unsafe-code audit
Rather than synthesizing our own unsafe code conventions, we follow the guidelines outlined in the following two resources:
In a nutshell:
unsafefunctions are required to include/// # Safetydocumentation describing any preconditions the caller must uphold when calling the function.unsafe {}blocks are required to include a// SAFETY:comment describing how the preconditions for calling theunsafefunction(s) within the block are being satisfied.expect(unsafe_code)annotations are required to include an// UNSAFETY:comment justifying why the code in question needs to useunsafe. This annotation must be placed at the module or crate level.
These requirements are enforced by CI, and will cause the build to fail if required documentation is missing.
Editing a file containing unsafe code will trigger CI to label your PR and warn reviewers that the PR touches unsafe code. This is to ensure that all unsafe code is audited for correctness by area experts.
Uses of cfg(target_arch = ...) must be justified
Checked Automatically: Yes (via cargo xtask fmt house-rules)
Unless you're working on something that's genuinely tied to the host's CPU
architecture, you should use cfg(guest_arch = ...) instead of cfg(target_arch = ...).
OpenVMM is a multi-architecture VMM framework, capable of running running x64 guests on a x64 host, as well as Aarch64 guests on Aarch64 hosts (with the potential of adding additional platforms in the future).
At the moment, OpenVMM requires that the host architecture and guest architecture match. That said, it's possible that at some point in the future, OpenVMM may also support mismatched guest/host architectures, via an emulated CPU virtualization backend (akin to QEMU).
Having an emulated CPU backend would enable OpenVMM to support such useful scenarios as:
- running Arch64 guests on x86 machines
- running x86 guests on ARM
- running something exotic (e.g: RISC-V) on x86/ARM machines
- ...assuming we had the bandwidth to implement + maintain something like that
- running OpenVMM on systems without hardware-accelerated CPU virtualization enabled
With these scenarios in mind, it would be short-sighted to rely entirely on
cfg(target_arch = ...) to gate guest-facing arch-specific functionality, as it
would inexorably tie the guest's arch to the host's arch, making any future
initiatives to pry the two apart significantly more difficult!
As such, the OpenVMM repo includes infrastructure to specify a custom,
OpenVMM-specific cfg(guest_arch = ...) cfg parameter.
By default, cfg(guest_arch = ...) will act the same way as cfg(target_arch = ...), but it can be swapped to a different architecture by setting the
OPENVMM_GUEST_TARGET env var at compile-time.
There are very few reasons to use cfg(target_arch = ...) within the OpenVMM
repo, and to enforce this rule, we have an in-house xtask fmt house-rules
check that lints each use of cfg(target_arch = ...) to include a
"justification" for why it's being used.
e.g: cfg(target_arch = ...) would be applicable when feature-gating a CPU
intrinsic (such as CPUID, or a SIMD instruction), or when implementing a
*-sys crate where the underlying C API/ABI varies between architectures.
...otherwise, use cfg(guest_arch = ...)!
Avoid Default when using zerocopy::FromZeros
Checked Automatically: No
The rule:
- A type can
derive(Default)XORderive(FromZeros). - A type that is
FromZeroscan alsoimpl Default, but it must be a conscious, explicit choice, with justification (read: inline comment) as to why that particular default value was chosen. - N.B.
derive(IntoBytes)orderive(FromBytes)implyderive(FromZeros). That is: this convention applies to those types as well.
The why:
- The all-zero type is often not a semantically valid
Defaultvalue for a type - There are plenty of types that don't have a
Defaultvalue, but do have a valid all-zero repr
Additional context
As per the Rust docs for Default::default:
fn default() -> Self
Returns the “default value” for a type.
Default values are often some kind of initial value, identity value, or anything else that may make sense as a default.
Notably, default should not be used as some shorthand to "zero initialize"
values! For most non-trivial structs, the all-zero representation is not a
semantically valid Default!
This is true in many contexts... but one that's particularly relevant in OpenVMM is that of FFI via C-style APIs and ABIs.
In C, it's very common for types to undergo multi-stage instantiation, where they are initially allocated as all-zero, and then get "filled in" by some secondary init code. Notably: it's quite rare for that initial "all-zero" struct to be a valid instance of the type!
Example: C FFI
For example, a common pattern in C libraries might look something like:
struct Handle {
uint16_t opaque_handle;
}
struct Handle handle = {0};
init_handle(&handle);
update_handle(handle, options);
do_thing(handle);
In this example: it would be an error to invoke update_handle or do_thing
with an all-zero handle, as the type hadn't finished being fully initialized.
If we wanted to use this library from Rust, a "naive" approach would be to do something like:
#[repr(C)]
#[derive(Default)]
struct Handle {
opaque_handle: u16,
}
let mut handle = Handle::default(); // BAD!
unsafe { init_handle(&handle) };
unsafe { update_handle(handle, options) };
unsafe { do_thing(handle) };While this technically works... using Default here is kinda bogus!
After all - Handle::default() doesn't actually call init_handle, which means
the value returned by default() doesn't match the "promise" of the trait!
Namely: the returned value is not semantically valid yet!
In many other Rust codebase, this "overloading" of Default to represent both
semantically valid value and all-zero values (in FFI) is par for the course,
as once structs get more complicated, having a derive that is able to fully
init a "uninitialized" struct in-memory is quite handy...
In OpenVMM, we don't do this. Instead, we use a separate trait to init all-zero structs.
In OpenVMM, we use FromZeros and FromZeros::new_zeroed() to work with types
that have valid all-zero representations, without implying that those types
also have valid all-zero default values!
So, for the example above:
#[repr(C)]
#[derive(zerocopy::FromZeros)]
struct Handle {
opaque_handle: u16
}
let mut handle = Handle::new_zeroed(); // GOOD!
unsafe { init_handle(&handle) };Now, it's impossible for code elsewhere to obtain a Handle via
Handle::default, and mistakenly forget to invoke init_handle on it.
...but if it so happens that we do want a Default impl for Handle, we can
do so by manually implementing derive(Default) ourselves:
// Default + FromZeros: `default` returns fully initialized handle
impl Default for Handle {
fn default() -> Handle {
let mut handle = Handle::new_zeroed();
unsafe { init_handle(&handle) };
handle
}
}Avoid Requiring Debug on Traits
Checked Automatically: No
TL;DR: Don't do this:
trait MyTrait: std::fmt::DebugImplementations of the standard library's Debug trait can be surprisingly large,
and the final binary size of OpenHCL and related binaries is a major concern
for us. Unused implementations of this trait are usually removed during the
optimization process (like all dead code), making this a non-issue. However when
traits, and more specifically trait objects, are involved, the compiler has a
much more difficult time proving that implementations are unused. This can
result in large amounts of functionally dead code ending up in the final
binaries.
If you need to implement Debug for a struct containing such a trait object, you
will need to do so manually, so that you can skip over that field.
Moreover, it's usually not good form to leave tracing statements that log a
struct's Debug representation in production. Prefer tracing just the fields
you're interested in, and/or connecting objects to the Inspect graph.
Crate Naming
Checked Automatically: Yes (via cargo xtask fmt house-rules)
Crates must be named with underscores, not dashes and underscores used in folder names.
- Bad:
my-cool-crate - Good:
my_cool_crate
Rust does not allow dashes in imports, with any dashes getting replaced with underscores when used in the code. Avoiding dashes altogether makes it easier to grep for crate names, and makes things more consistent across the repo.
This convention is enforced by CI
Do not name crates with the words "base, util, common" or other terms that are overly general.
For example, consider a crate that provides a common data structure used by multiple devices:
- Bad:
devices_common - Good:
range_map
Libraries that contain the following eventually become a mishmash of unrelated functionality that is located there for convenience. This blog post goes more in-depth as to why.
Instead, name things based on what they logically provide, like functionality or data types.
Release Gates Workflow
Triggered Manually: Yes (via GitHub labels)
In addition to the standard PR gates that run in debug mode, OpenVMM also provides a "Release Gates" workflow that runs the same checks but compiled in release mode. This workflow takes significantly longer to run but can catch issues that only manifest in optimized builds.
When to Use Release Gates
The release gates workflow should be used when:
- Making changes to performance-critical code paths
- Modifying compiler flags or build configuration
- Implementing low-level optimizations
- Debugging issues that only appear in release builds
- Before merging large refactoring changes
How to Trigger Release Gates
To run the release gates on your PR:
- Ensure your PR is ready for review (not in draft mode)
- Add the
release-ci-requiredlabel to your PR - The workflow will automatically trigger and run all checks in release mode
The workflow will only run when the specific label is present, so you have full control over when to use this more resource-intensive testing.
Label Management
Only repository maintainers can add labels to PRs. If you need release gates
run on your PR, ask a maintainer to add the release-ci-required label for you.
Save State
OpenHCL supports the mechanism of saving & restoring state. This primitive can be used for various VM operations, but a key use case is for updating OpenHCL at runtime (a.k.a. "Servicing"). This save state can be stored in memory or on durable media, read back at a later time.
Save State First Principles
Here are the principles you must maintain when adding new save & restore code:
- Save & Restore is Forward & Backwards Compatible: A newer version of OpenHCL must understand save state from a prior version, and an older version must not crash when reading save state from a newer version.
- Do not break save state after that state is in use: Save state must be compatible from any commit to any other commit, once the product has shipped and started using that save state.1
- All Save State is Protocol Buffers: All save state is encoded as
ProtoBuf, usingmesh.
Best practices
- Put save state in it's own module: This makes PR reviews easier, to catch any mistakes updating save state.
- Create a unique package per crate: A logical grouping of saved state
should have the same
package - Avoid unsupported types, when possible: These types don't support the
default values needed for safely extending save state:
- Arrays: if you need to add an array, consider a
vecorOption<[T; N]>instead. - Enum: if you need to add an enum, add it as
Option<MyEnum>instead.
- Arrays: if you need to add an array, consider a
- Be particularly careful when updating saved state: See below.
Updating (Extending) Saved State
Since saved state is just Protocol Buffers, use the guide to updating Protocol Buffers messages as a starting point, with the following caveats:
- OpenVMM uses
sint32to represent thei32native type. Therefore, changingi32tou32is a breaking change, for example. - The Protocol Buffers docs mention what happens for newly added fields, but it
bears adding some nuance here:
- Plain
arraysandenumsare not supported. Reading newer save state with anarrayorenumwill fail on an older build. Instead, wrap these in anOption. - Old -> New Save State: Save state from a prior revision will not contain
some newly added fields. Those fields will get the default
values. This is
how that breaks down for the rust types:
Option<T>=>None- Structs => each field gets that field's default value
- Vecs => empty vec
- Numbers => 0
- Strings =>
""
- New -> Old Save State: Unknown fields are ignored.
- Plain
- Ensure that default values for new saved state fields make semantic sense.
Here is the heuristic: if you need a conditional to check if the restored
value is the default because it was not included in save state, you should
use an
Option. If you wouldn't otherwise need a conditional, you should not use anOption. - Define your saved state so that the natural default of
booltypes isfalse.
Defining Saved State
Saved state is defined as a struct that has #[derive(Protobuf)] and
#[mesh(package = "package_name")] attributes. Here is an example, taken from
the nvme_driver:
pub mod save_restore {
use super::*;
/// Save/restore state for IoQueue.
#[derive(Protobuf, Clone, Debug)]
#[mesh(package = "nvme_driver")]
pub struct IoQueueSavedState {
#[mesh(1)]
/// Which CPU handles requests.
pub cpu: u32,
#[mesh(2)]
/// Interrupt vector (MSI-X)
pub iv: u32,
#[mesh(3)]
pub queue_data: QueuePairSavedState,
}
}Saved state is in use when it reaches a release branch that is in tell mode. See release management for details.
Release Management
Occasionally, the OpenVMM project will declare upcoming release milestones. We
stabilize the code base in a release/<MAJOR>.<MINOR>.<YYMM> branch, typically
named for the YYMM when the branch was forked. Future references to the release
number will be shortened to <RELEASE> in this doc. We expect a high quality
bar for all code that goes into the OpenVMM main branch, and we ask developers
to hold these release branches to the highest quality standards. The OpenVMM
maintainers will gradually slow the rate of churn into these branches as we get
closer to a close date.
Note: Some older release branches use the format
release/<YYMM>without the major and minor version numbers (e.g.,release/2411,release/2505).
This process should not impact your typical workflow; all new work should go
into the main branch. But, to ease the cherry-picks, we may ask that you hold
off from making breaking or large refactoring changes at points in this
process.
Marking, Approval Process, Code Flow
The OpenVMM maintainers will publish various dates for the upcoming releases. Currently, these dates are driven by a Microsoft-internal process and can, and do, often change. Microsoft does not mean to convey any new product launches by choices of these dates.
Releases naturally fall into several phases:
| Phase | Meaning |
|---|---|
| Active Development | Regular development phase where new features and fixes are added. |
| Stabilization | Phase focused on stabilizing the release by fixing bugs. |
| Ask Mode | Only critical fixes are allowed; changes are scrutinized. No new features. This is the last phase before a release is closed. |
| Servicing | Only essential fixes are made to support the release (a.k.a. maintenance mode). |
| Out of service | A previous release which is no longer receiving updates. |
Release branch process
We track the state of candidates for a given release by tagging the PRs with the following labels:
backport_<RELEASE>: This PR (tomain) is a candidate to be included in the release.- N.B.: A maintainer will remove this tag if the fix is not accepted into the release.
backported_<RELEASE>: This PR (tomain) has been cherry-picked to the release branch.
Seeking Approval for Backport
To seek approval to include a change in a release branch, follow these steps:
- Tag your PR to
mainwith thebackport_<RELEASE>label. - Wait for the PR to be merged to
main. - Cherry-pick the change to the appropriate release branch in your fork and stage a PR to that same branch in the main repository.
Please reach out to the maintainers before staging that PR if you have any doubts.
Backport PR Best Practices
When creating a backport PR to a release branch:
- Clean cherry-picks are strongly preferred. A clean cherry-pick minimizes reviewer effort and reduces the risk of introducing regressions.
- If the backport is not a clean cherry-pick (e.g., requires conflict resolution or additional modifications), clearly indicate this in the PR description. This signals to the reviewer that extra care is needed during the review process.
Existing Release Branches
| Release | Phase | Notes |
|---|---|---|
| release/2411 | Out of service | |
| release/2505 | Servicing | Supports runtime servicing from release/2411. |
| release/1.7.2511 | Stabilization | Supports runtime servicing from release/2411 and release/2505. |
| tbd, in main | Active Development | Supports runtime servicing from release/2411 and release/2505. |
Taking a Dependency on a Release
We welcome feedback, especially if you would like to depend on a reliable release process. Please reach out!
Submitting Changes
Follow the CONTRIBUTING guide.
Code Review Guidance
The Code Review Process
Although the OpenVMM repository requires a maintainer to sign off before a pull request can be merged, this does not mean non-maintainer reviews are not valuable. It is extremely important for the health of the project for people to review areas of code they are familiar with. For example, for a change that touches multiple components, somebody familiar with one component could leave a review that says, "The changes to component A look good, but I'm not familiar with the rest of the code." These types of reviews are still extremely useful and help move changes forward. Maintainers will also feel more confident merging changes once subject-area experts have weighed in.
Submitter's Responsibility
If your patch or change isn’t gaining traction, it is your responsibility as the submitter to follow up and ensure the right people review your changes. This means sending polite reminders to potential reviewers. Do not rely on GitHub notifications for this because people may have them filtered or disabled. The OpenVMM repository has a CODEOWNERS file, which will automatically add teams to the review for some components. If you are unsure who the correct audience for the review is, please ask for guidance from maintainers or other contributors.
Updating this Guide
We gladly welcome PRs that improve the quality of the OpenVMM guide!
The OpenVMM Guide is written in Markdown, and rendered to HTML using
mdbook. You can find the source-code of
this Guide in the main OpenVMM GitHub repo, in the
Guide/ folder.
Guide conventions
- Line Length: Wrap lines at 80 characters.
Editing the Guide
Small Changes
For small changes, you can simply click the "Suggest an Edit" button in the top-right corner of any page to automatically open up a GitHub Edit page.
Medium Changes
For medium changes, we suggest cloning the repo locally, and previewing changes to Markdown in your editor (Visual Studio Code has good support for this).
Large Changes
For large changes, we suggest cloning the repo locally, and building a fully
rendered copy of the Guide using mdbook.
This is very useful when making changes that leverage mdbook preprocessors, such as using mermaid diagrams, or previewing admonishments.
Building the Guide locally is quite straightforward:
- Install
mdbookand the additional preprocessors we use locally:
cargo install mdbook
cargo install mdbook-admonish
cargo install mdbook-mermaid
- Navigate into the
Guide/directory, and runmdbook:
cd Guide/
# must be run inside the `Guide/` directory!
mdbook serve
- Navigate to the localhost URL in your web browser (typically
http://127.0.0.1:3000/)
Troubleshooting
Running mdbook serve outside the Guide/ directory
Error:
2024-10-29 16:26:22 [INFO] (mdbook::book): Book building has started
error: manifest path `./mdbook-openvmm-shim/Cargo.toml` does not exist
Solution:
Ensure you have changed your working-directory to the Guide/ folder (e.g: via
cd Guide/), and then run mdbook serve.
Rust is not installed
Error:
2024-10-29 16:35:49 [INFO] (mdbook::book): Book building has started
2024-10-29 16:35:49 [WARN] (mdbook::preprocess::cmd): The command wasn't found, is the "admonish" preprocessor installed?
2024-10-29 16:35:49 [WARN] (mdbook::preprocess::cmd): Command: cargo run --quiet --manifest-path ./mdbook-openvmm-shim/Cargo.toml mdbook-admonish
Solution:
The OpenVMM Guide hooks into a custom Rust utility called mdbook-openvmm-shim,
which must be compiled in order for mdbook to successfully build the OpenVMM
guide.
Please ensure you have installed Rust.
OpenVMM Features
This section discuss various features that are exclusive to OpenVMM.
Configuration and Management
OpenVMM's configuration and management interfaces are currently unstable, incomplete, lightly documented, and broadly speaking - not particularly "polished".
These interfaces are strictly for dev use only.
Refer to the OpenVMM disclaimer for more context.
At the moment, OpenVMM exposes 3 distinct configuration and management interfaces.
- CLI: Used to configure and launch a single VM
- This allows configuring static VM resource assignments, such as the number of processors, RAM size, UEFI, graphic console, etc.. as well as what devices are exposed to the Guest, such as a virtual NIC, Storage, vTPM, etc..
- Interactive console: Used to interact with a VM at runtime
- This interface allows users to perform core VM operations such as stop, restart, save, restore, pause, resume, etc.. as well as things like storage hot-add, VTL2 servicing, running Inspect queries, etc..
- gRPC / ttrpc: A very WIP set of APIs for configuring and interacting with VMs
Missing Functionality (non-exhaustive)
The following is a non-exhaustive list of notable management features that OpenVMM is currently missing.
| Feature | Status |
|---|---|
| Suspend / Resume a VM | OpenVMM's existing save/restore infrastructure theoretically supports this, but the end-to-end flow has not been wired up to any management interface at the moment. |
| Snapshots | OpenVMM has core infrastructure for performing save/restore operations, but there are gaps in device support (notably: no support for storage snapshots). |
| Managing multiple running VMs |
OpenVMM currently runs a single VM per-process. It is not yet clear whether OpenVMM will support managing multiple VMs via a single OpenVMM process, or if OpenVMM will rely on external management tools (e.g: `libvirt`) interfacing with its existing APIs in order to launch and manage multiple VMs. |
If a feature is missing from this list, please check if the feature is being tracked via a Issue on the OpenVMM GitHub, and/or submit a PR adding it to this list.
CLI
The following list is not exhaustive, and may be out of date.
The most up to date reference is always the code itself,
as well as the generated CLI help (via cargo run -- --help).
--processors <COUNT>: The number of processors. Defaults to 1.--memory <SIZE>: The VM's memory size. Defaults to 1GB.--hv: Exposes Hyper-V enlightenments and VMBus support.--uefi: Boot usingmu_msvmUEFI--pcat: Boot using the Microsoft Hyper-V PCAT BIOS--disk file:<DISK>: Exposes a single disk over VMBus. You must also pass--hv. TheDISKargument can be:- A flat binary disk image
- A VHD file with an extension of .vhd (Windows host only)
- A VHDX file with an extension of .vhdx (Windows host only)
--nic: Exposes a NIC using the Consomme user-mode NAT.--virtio-console: Enables a virtio serial device (via the MMIO transport) for Linux console access instead of COM1.--virtio-console-pci: Uses the PCI transport for the virtio serial console.--gfx: Enable a graphical console over VNC (see below)--virtio-9p: Expose a virtio 9p file system. Uses the formattag,root_path, e.g.myfs,C:\\. The file system can be mounted in a Linux guest usingmount -t 9p -o trans=virtio tag /mnt/point. You can specify this argument multiple times to create multiple file systems.--virtio-fs: Expose a virtio-fs file system. The format is the same as--virtio-9p. The file system can be mounted in a Linux guest usingmount -t virtiofs tag /mnt/point. You can specify this argument multiple times to create multiple file systems.
And serial devices can each be configured to be relayed to different endpoints:
--com1/com2/virtio-serial <none|console|stderr|listen=PATH|listen=tcp:IP:PORT>none: Serial output is dropped.console: Serial input is read and output is written to the console.stderr: Serial output is written to stderr.listen=PATH: A named pipe (on Windows) or Unix socket (on Linux) is set up to listen on the given path. Serial input and output is relayed to this pipe/socket.listen=tcp:IP:PORT: As withlisten=PATH, but listen for TCP connections on the given IP address and port. Typically IP will be 127.0.0.1, to restrict connections to the current host.
Interactive Console
By default, OpenVMM will connect the guests's COM1 serial port to the current terminal session, forwarding all keystrokes directly to the VM.
To enter OpenVMM's interactive command mode, launch OpenVMM, and type ctrl-q.
You can then type the following commands (followed by return):
The following list is not exhaustive and may be out of date.
The most up to date reference is always the code itself. For a full list of
commands, please invoke the help command.
q: quit. Note--sometimes this does not work due to a bug in the virito serial teardown path. In this case, type Ctrl-C to exit after runningq.I: re-enter interactive mode.i<LINE>: inputLINEto the active serial console.R: restart worker (experimental)n: inject NMIs: print stateh: print hv statep: pauser: resumed [-ro] [-path <INDEX>] [-target <INDEX>] [-lun <INDEX>] [-ram <Size>] <PATH>: hot add the disk at<PATH>to the VM. Requires--hvx [-r] [path]: inspect runtime state using theInspecttrait infrastructurehelp: help
gRPC / ttrpc
To enable gRPC or ttrpc management interfaces, pass --grpc <SOCKETPATH> or
--trpc <SOCKETPATH>. This will spawn an OpenVMM process acting as a gRPC or
ttrpc server.
Here is a list of supported RPCs:
The following list is not exhaustive, and may be out of date. The most up to
date reference is the vmservice.proto file.
Moreover, many APIs defined in the .proto file may not be fully wired up yet.
In other words: This API is very WIP, and user discretion is advised.
- CreateVM
- TeardownVM
- PauseVM
- ResumeVM
- WaitVM
- CapabilitiesVM
- PropertiesVM
- ModifyResource
- Quit
Graphical Console
OpenVMM supports a graphical console exposed via VNC. To enable it, pass --gfx
on the command line--this will start a VNC server on localhost port 5900. The
port value can be changed with the --vnc-port <PORT> option.
OpenVMM's VNC server also includes "pseudo" client-clipboard support, whereby the "Ctrl-Alt-P" key sequence will be intercepted by the server to type out the contents of the VNC clipboard.
Once OpenVMM starts, you can connect to the VNC server using any supported VNC client. The following clients have been tested working with OpenVMM:
Once you have downloaded and installed it you can connect to localhost with
the appropriate port to see your VM.
OpenVMM Logging
Configuring OpenVMM logging messages to emit
To configure logging, use the OPENVMM_LOG environment variable. For example:
Enables debug events from all modules:
set OPENVMM_LOG=debug
Enables trace events from the mesh crate and info events from everything else:
set OPENVMM_LOG=info,mesh=trace
This is backed by the
EnvFilter
type; see the associated documentation for more details.
Configuring OpenHCL Trace Logging
If OpenHCL is used, it also supports an EnvFilter style trace logging options that can be configured using the OPENVMM_LOG= command line variable passed during OpenHCL startup with -c OPENVMM_LOG=. The -c argument in OpenVMM passes a string of command line arguments to OpenHCL initialization.
The environment variable configuration and style of OPENVMM_LOG for OpenHCL is the same for configuring tracing for OpenVMM.
OpenHCL tracing can also be configured and dumped at runtime with ohcldiag-dev. See: OpenHCL Diagnostics
To retrieve OpenHCL log output at runtime, an output console or file must attach to the OpenHCL logging COM port. By default, OpenHCL outputs to COM3.
To open a new terminal window with global OpenHCL debug level tracing enabled:
openvmm.exe -c "OPENVMM_LOG=debug" --com3 "term,name=VTL2 OpenHCL" [...]
Configure log levels of only a given module name:
openvmm.exe -c "OPENVMM_LOG=mesh=trace" --com3 "term,name=VTL2 OpenHCL" [...]
Multiple modules can be specified by separating them with a comma:
openvmm.exe -c "OPENVMM_LOG=mesh=trace,nvme_driver=trace" --com3 "term,name=VTL2 OpenHCL" [...]
For more configuration examples of serial ports and the OpenVMM CLI, see the Running OpenHCL Guide and CLI --help output.
Capturing the ETW traces on the host
On Windows, OpenVMM also logs to ETW, via the Microsoft.HvLite provider.
To capture the trace first need to start the session:
logman.exe start trace <SessionName> -ow -o FileName0.etl -p "{22bc55fe-2116-5adc-12fb-3fadfd7e360c}" 0xffffffffffffffff 0xff -nb 16 16 -bs 16 -mode 0x2 -ets
For OpenHCL traces, use
{AA5DE534-D149-487A-9053-05972BA20A7C}as the provider GUID.
To flush:
logman.exe update <SessionName> -ets -fd
To stop:
logman.exe stop <SessionName> -ets
To decode as CSV:
tracerpt.exe <FileName0>.etl -y -of csv -o <FileName1>.csv -summary <FileName2>.summary
OpenHCL Features
This section discuss various features that are exclusive to OpenHCL.
Diagnostics
This chapter discusses several of the diagnostic tools available when working with OpenHCL.
Preface: CVM restrictions
When OpenHCL detects that it is running as a Confidential VM it will restrict the diagnostics it sends to the VM host. This is done in order to prevent any guest secrets from being leaked to the host.
Unless otherwise noted, all of the following restrictions only apply to release builds of OpenHCL for CVMs. The majority of these restrictions will not apply to debug builds of OpenHCL.
This is controlled by the enable_debug flag in the IGVM JSON definition.
Simulating CVM restrictions
Most of these restrictions can be simulated on a non-CVM OpenHCL VM by setting the
OPENHCL_CONFIDENTIAL environment variable to 1, either in your IGVM JSON definition or by
using the Set-VmFirmwareParameters cmdlet. This environment variable will cause OpenHCL to
behave as if it is running in a CVM for the purpose of diagnostics.
Tracing
Tracing statements and spans will still be sent to the host, and therefore will still show up in ETW traces and Kusto. However, individual statements may opt out of being logged inside a CVM, as a way of protecting guest secrets.
For Developers
This is done by using the CVM_CONFIDENTIAL constant provided by the
cvm_tracing crate. cvm_tracing also provides a CVM_ALLOWED constant, to
mark statements that do not contain secrets and can be logged in a CVM.
Examples:
use cvm_tracing::{CVM_ALLOWED, CVM_CONFIDENTIAL};
tracing::info!(CVM_ALLOWED, foo, ?bar, "This statement will be logged in a CVM");
tracing::info!(baz, "This statement will also be logged in a CVM");
tracing::info!(CVM_CONFIDENTIAL, super_secret, "This statement will not be logged in a CVM");
// This also works with spans.
let span = tracing::info_span!("a span", CVM_CONFIDENTIAL);
my_func.instrument(span).await;
// And the #[instrument] macro.
#[instrument(name = "foo", fields(CVM_CONFIDENTIAL))]
fn my_func() {
// ...
}Some of the tracing macros will not accept cvm_tracing::CVM_CONFIDENTIAL as an
argument.
Instead, you will need to use cvm_tracing::CVM_CONFIDENTIAL, and then use just
CVM_CONFIDENTIAL.
ohcldiag-dev
Most ohcldiag-dev commands will not work when connecting to a CVM.
One notable exception is the inspect command (albeit with restrictions).
inspect
The available inspect nodes for a CVM are restricted to prevent exposing guest data.
The vm/ top-level node is inaccessible, however most nodes containing
information about the VTL2 processes are still available.
Crash information
Crash dumps can leak quite a bit of information, and as such, are heavily restricted in CVMs.
Dumps
Crash dumps will not be generated when a crash occurs in a CVM's VTL2.
Hyper-V MSRs
The Hyper-V crash MSRs will still be set when a crash occurs in a CVM's VTL2, but the data values will be sanitized to prevent leaking guest secrets. This will result in Hyper-V logging that a crash occurred, but there will be no debugging information available.
NOTE: This restriction also applies to debug builds of OpenHCL when running a CVM.
NOTE: This restriction cannot be simulated using
OPENHCL_CONFIDENTIAL.
Saved state
Extracting the save state of a CVM is not supported. This applies both to the ohcldiag-dev save command,
and to the save-on-crash registry key.
ohcldiag-dev
OpenHCL includes a "diag server", which provides an interface to diagnose and interact with the OpenHCL binary and user-mode state.
ohcldiag-dev is the "move-fast, break things" tool used by the core OpenHCL
dev team, and as such, it makes NO stability guarantees as to the specific
format of the CLI, output via stdout/stderr, etc...
That is to say:
ANY AUTOMATION THAT ATTEMPTS TO USE ohcldiag-dev WILL EVENTUALLY BREAK!
ochldiag-dev is designed to work no matter where you run OpenHCL: in a Hyper-V
VM, an OpenVMM VM using VSM or nested virtualization, or in other VMMs that
support paravisors. Consider the hypestv tool for an interactive dev/test
tool specifically for Hyper-V VMs.
Examples
Check OpenHCL version
You can inspect a running OpenHCL VM with ohcldiag-dev.
PS > .\ohcldiag-dev.exe <vm name> inspect build_info
{
crate_name: "underhill_core",
scm_revision: "bd7d6a98b7ca8365acdfd5fa2b10a17e62ffa766",
}
You can use that to validate your VM is running with the OpenHCL image you intended by checking the scm-revision output matches the commit hash of the OpenHCL repo (if building OpenHCL, you can get the commit hash of your repo using git log --max-count=1).
The detailed kernel version information is available from the initial RAM filesystem only:
PS > .\ohcldiag-dev.exe <vm name> run -- cat /etc/kernel-build-info.json
{
"git_branch": "rolling-lts/underhill/5.15.90.7",
"git_revision": "55792e0aa5e92ac4450dc10bf032caadc019fd84",
"build_id": "74486489",
"build_name": "5.15.90.7-hcl.1"
}
The OpenHCL version information can be read from the filesystem, too:
PS > .\ohcldiag-dev.exe <vm name> run -- cat /etc/underhill-build-info.json
{
"git_branch": "user/romank/kernel_build_info",
"git_revision": "a7c4ba3ffcd8708346d33a608f25b9287ac89f8b"
}
Interactive Shell
To get an interactive shell into the VM, try:
ohcldiag-dev.exe <vm name> shell
Interactive shell is only available in debug builds of OpenHCL.
Running a command
To run a command non-interactively:
ohcldiag-dev.exe <vm name> run cat /proc/interrupts
Using inspect
To inspect OpenHCL state (via the Inspect trait):
ohcldiag-dev.exe <vm name> inspect -r
kmsg log
The kernel kmsg log currently contains both the kernel log output and the
OpenHCL log output. You can see this output via the
serial console, if you have it configured, or via ohcldiag-dev:
ohcldiag-dev.exe <vm name> kmsg
If you want a continuous stream of output as new messages arrive, pass the -f
flag:
ohcldiag-dev.exe <vm name> kmsg -f
By default, the OpenHCL logs will only contain traces at info level and
higher. You can adjust this globally or on a module-by-module basis. And you can
set the tracing configuration at startup or dynamically with ohcldiag-dev.
To set the trace filter at startup, add a kernel command line option
OPENVMM_LOG=<filter>. To update it on a running VM, run:
ohcldiag-dev.exe <vm name> inspect trace/filter -u <filter>
The format of <filter> is a series of comma-separated key-value pairs, plus an
optional default, <default-level>,<target>=<level>,<target>=<level>. <level>
can be one of:
tracedebuginfowarnerroroff
<target> specifies the event or span's target, which defaults to the fully
qualified module name (including the crate name) that contains the event, but it
can be overridden on individual trace statements.
So to enable warning traces by default, but debug level for storvsp traces, try:
ohcldiag-dev.exe <vm name> inspect trace/filter -u warn,storvsp=debug
If successful, the new filter will take effect immediately, even if you have an
open kmsg session already.
Note: release builds have trace level compiled out by default, so
trace-level events cannot be enabled dynamically. To build a custom release
build with trace-level events available, you can use the --max-trace-level
parameter to cargo xflowey build-igvm:
cargo xflowey build-igvm x64 --release --max-trace-level trace
This is not necessary for debug builds.
Network packet capture (PCAP)
PCAP is an industry standard format for capturing network packets. OpenHCL now supports PCAP based packet capture for the network packets that are going through it.
Prerequisites
- PCAP based packet capture support in OpenHCL came in around Nov 2023. The easiest
way to check whether the OpenHCL version you are running has PCAP support or not is by
running
ohcldiag-dev -hand if the output shows an option forpacket-capture, then the support is there. Otherwise, pick a newer version of OpenHCL. - OpenHCL PCAP support is only for the synthetic network path. It will likely not show any packets captured if a vNIC is operating in accelerated networking mode. If you would like to capture the network packets for a given vNIC in OpenHCL, disable accelerated networking on the vNIC first.
Packet capture options
To see the options for packet capture, run the help command using:
ohcldiag-dev packet-capture -h
The help should be self explanatory, but further below are some sample commands for reference purposes.
How to stop running packet capture
There are two ways of controlling how long the packet capture runs.
- Use the
-Gor--secondsto specify for how many seconds to run the packet capture for in the command line. If not specified, it runs for the default value, which you can see from the output of the help command above. This option can be handy for example, when doing packet capture on the TiP node, where interacting with the console using keys likeCtrl+cis not possible. - If you would like to keep the packet capture running indefinitely, specify a big value
for the
-Goption. You can then stop the capture at any time using theCtrl+ckey.
Packet capture traces
The packet capture command will generate a pcap file for each vNIC. You can control the
name of the pcap file generated using the -w option. If not specified, the default
value for the file name is shown by the help command above. The index of the vNIC is
appended to the file name. So, for example, the pcap file for the first vNIC would be
<default value>-0.pcap, the second one <default-value>-1.pcap, so on and so forth.
Loading the pcap file for analysis
There are many software that are available to load the pcap file. The most commonly
used one is wireshark. Copy the *.pcap files generated on the test machine and then
open them up on the desired software.
Example packet capture commands
In all of the below commands, $vmname should be replaced with the actual VM name. On
Azure, the VM name is the same as the container ID.
- Most basic command; run packet capture with all defaults. This will run packet capture for the default values, including the default time (see the help command above for default values).
ohcldiag-dev.exe $vmname packet-capture
- Run packet capture indefinitely and use Ctrl+c to stop.
ohcldiag-dev.exe $vmname packet-capture -G 655555
- Run packet capture with the location of the output location using the
-woption. By default, the traces are captured in the current working dir. That may not always be desirable, especially on TiP. Let's say you want all the output pcap files to go to thec:\testfolder, then you can do something like:
ohcldiag-dev.exe ubuntu packet-capture -w c:\test\nic
The output files will be of the form c:\test\nic-*.pcap
- Specify the length of the packet to capture using the
-sor--snaplenoption. By default, the length of the packet captured can be big and can cause the size of the pcap files to be quite large. It is advisable to only capture the packets for the length that is of interest. For example, to specify only capturing 128 bytes of the packet (which will generally give you the TCP and IP headers), do:
ohcldiag-dev.exe ubuntu packet-capture -s 128
- Run the packet capture for the specified duration in seconds using the
-Goption. For example, to capture packets for 2min, do:
ohcldiag-dev.exe ubuntu packet-capture -G 120
Performance analysis
Besides performance analysis for VTL0 VM and host OS, we'd like to capture trace
inside VTL2 as well. This allows us to analyze the Linux kernel and
openvmm_hcl worker process inside VTL2.
Prerequisite for capturing perf data
The release Linux image doesn't have user mode perf program by default. To capture perf data inside VTL2, it is necessary to build OpenHCL with the below instructions, which will include the necessary programs.
cargo xflowey build-igvm [RECIPE] --release --with-perf-tools
Increase VTL2 memory page count
To capture and save perf data file inside VTL2, we need to increase VTL2's memory page count by increasing the memory_page_count value in the IGVM configuration file (openhcl-x64-dev.json). E.g. increase it to 524288 like:
{
"image": {
"openhcl": {
....................
"memory_page_count": 524288
}
}
}
Capture perf data inside VTL2
While workloads run inside VTL0 VM, use ohcldiag-dev.exe to run perf to capture perf_events profiling data inside VTL2. E.g. the following command captures 15s of perf data and saves it in a file. You can find more info about perf on external page perf Examples
.\ohcldiag-dev.exe <VM Name> run -- perf record -F 999 -a --call-graph=dwarf -o ./openhcl.fio.perf -- sleep 15
Use perf to convert perf data to plain text and dump it to a file on host
.\ohcldiag-dev.exe <VM Name> run -- perf script -i ./openhcl.fio.perf > .\traces\openhcl.fio.perf.script
Visualize perf profiling data
Please follow up instructions on the external page Flame Graphs to create flame graph SVG file. It requires scripts from FlameGraph GitHub repo, so it is better to do it on WSL2.
Here is an example command on WSL2. It converts the perf script file to SVG file. Both of files are located under d:\tmp\vtl2 folder on Windows.
perf_file=/mnt/d/tmp/vtl2/openhcl.fio.perf.script; cat $perf_file | ./stackcollapse-perf.pl > $perf_file.folded; cat $perf_file.folded | ./flamegraph.pl > $perf_file.svg
If the perf script file doesn't have rust functions demangled correctly, please add rustfilt in the pipe to assist demangling.
perf_file=/mnt/d/tmp/vtl2/openhcl.fio.perf.script; cat $perf_file | rustfilt | ./stackcollapse-perf.pl > $perf_file.folded; cat $perf_file.folded | ./flamegraph.pl > $perf_file.svg
OpenHCL Tracing
Using ohcldiag-dev
ohcldiag-dev offers several methods for collecting
different sorts of traces from OpenHCL.
We suggest starting here, before exploring some of the other options presented on this page.
Enabling serial logging for OpenHCL
The OpenHCL startup binary accepts a commmand line argument OPENVMM_LOG that can be used to enable global or discrete tracing levels.
These logs are written by default to COM3 and OpenVMM can be configured to redirect them to a file or console output.
For examples on how to enable OPENVMM_LOG, see OpenVMM Logging.
What about Hyper-V?
Hyper-V only supports 2 COM ports for production scenarios. If you are on Windows Insider build 28000 or higher, you can do the following. (This is how we get COM3 output in our CI runs.)
reg.exe add "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Virtualization" /v EnableAdditionalComPorts /t REG_DWORD /d 1 /f
$com3Pipe = "\\.\pipe\openhcl-com3"
Set-VMComPort -VMName $VmName -Number 3 -Path $com3Pipe
# Pipe serial out to the console, for example using the built-in tool `hvc.exe`... (you could use hypestv or other tools as well)
hvc serial -c -p 3 -r $VmName
[Hyper-V] Saving traces to the Windows event log
The OpenHCL traces can be saved to the Windows event log on the host. That is not meant to be a production scenario due to resource consumption concerns. By default, only ETW is emitted.
Setting PersistentGel under the virt. key (HKLM:SOFTWARE\Microsoft\Windows NT\CurrentVersion\Virtualization)
to 1 (REG_DWORD) makes the messages being stored to the host event log, too, to make getting traces
easier in the development scenarios. The traces will be stored under the Hyper-V Worker Operational log.
Here is a Powershell one-liner to enable that developer aid:
New-ItemProperty "HKLM:SOFTWARE\Microsoft\Windows NT\CurrentVersion\Virtualization" -Name "PersistentGel" -Value 1 -Type Dword -Force
Note: the key has to be set prior to starting the VM to save the logging messages sent by VTL2 running inside that VM to the Windows event log.
To retrieve the events with Powershell, start with this one-liner and tweak it to your needs:
Get-WinEvent -FilterHashtable @{ LogName='Microsoft-Windows-Hyper-V-Worker-Operational'; ProviderName='Microsoft-Windows-Hyper-V-Chipset' }
(Advanced) Enable Linux Kernel Tracing
Sometimes it can be useful to extract additional information from the kernel during runtime. By default the config OpenHCL uses does not support tracing; as such you will need to build a custom kernel with tracing support. First, see the Kernel Development section of the docs to find the repo. To set up a tracing enabled kernel:
- Find
CONFIG_FTRACEin Microsoft/hcl-dev.config and change it fromCONFIG_FTRACE is not settoCONFIG_FTRACE=y. - Build the kernel using the Microsoft/build-hcl-kernel.sh script.
- In the loader json you intend to use, change the
kernel_pathentry to point to your newly built vmlinux. This can usually be found at linux-dom0-hyperv/out/vmlinux. - Build OpenHCL using
cargo xflowey build-igvm --custom-kernel path/to/vmlinux. - When launching your OpenHCL vm, be sure to Set-VmFirmwareParameters
correctly. The following is an example that enables tracing hyper-v linux
components such as vmbus:
tp_printk=1 trace_event=hypervtp_printk=1tells the kernel to print traces to the kernel log.trace_events=<module>tells the kernel which module traces to print.
Hardware Debugging (gdbstub)
Think EXDI from Hyper-V, except instead of using the EXDI interface, we use the
GDB Remote Serial Protocol
(via the gdbstub Rust library).
Hardware debugging has several benefits over using an in-guest / in-kernel debugger:
- Debugging early-boot scenarios (before UEFI / Windows / Linux debuggers are set up)
- Debugging low-level ISRs
- Non-intrusive debugging = easier to repro certain bugs
- Debugging SNP/TDX/VBS Confidential VMs
Enabling the Debugger
OpenVMM
- Pass the
--gdb <port>flag at startup to enable the debug worker. e.g.,--gdb 9001
To pause the VM until the debugger has been attached, pass --paused at startup.
OpenHCL
- Pass the
OPENHCL_GDBSTUB=1OPENHCL_GDBSTUB_PORT=<gdbstub port>parameters to enable gdbstub. e.g.,Set-VmFirmwareParameters -Name UhVM -CommandLine OPENHCL_GDBSTUB=1 OPENHCL_GDBSTUB_PORT=5900. - To expose a TCP port, run
ohcldiag-dev.exe <name> vsock-tcp-relay --allow-remote --reconnect <gdbstub port> <tcp port>.
To pause VTL0 boot until desired, pass OPENHCL_VTL0_STARTS_PAUSED=1 as a parameter. Then once the debugger is attached, you can start VTL0 with ohcldiag-dev.exe <name> resume.
Connecting via GDB
The quickest way to get connected to a OpenVMM VM is via gdb directly.
Note that GDB does not support debugging PDBs, so if you're trying to debug
Windows, you'll be limited to plain disassembly. See the Connecting via WinDbg section below if this is your use-case.
On the flipside, if you're trying to debug ELF images with DWARF debug info
(e.g., a vmlinux binary), then you'll likely want to use gdb directly, as it
will support source-level debugging with symbols, whereas WinDbg will not.
You can install gdb via your distro's package manager. e.g., on Ubuntu:
sudo apt install gdb
Once gdb is installed, run it, and enter the following gdb command (swapping
9001 for whatever port you specified at the CLI)
target remote :9001
If all goes well, you should get output similar to this:
(gdb) target remote :9001
Remote debugging using :9001
warning: No executable has been specified and target does not support
determining executable automatically. Try using the "file" command.
0xfffff8015c054c1f in ?? ()
(gdb)
At this point, you can try some basic GDB commands to make sure things are working.
e.g., start / interrupt the VM's execution using cont and ctrl-c
(gdb) cont
Continuing.
^C # <-- hit ctrl-c in the terminal
Thread 1 received signal SIGINT, Interrupt.
0xfffff8015c054c1f in ?? ()
(gdb)
e.g., inspecting register state
(gdb) info registers
rax 0x0 0
rbx 0x0 0
rcx 0x40086 262278
rdx 0x0 0
rsi 0xffff960d4eea5010 -116491073990640
rdi 0x0 0
rbp 0x0 0x0
rsp 0xfffff8015b3f5ec8 0xfffff8015b3f5ec8
r8 0x0 0
r9 0xffffffff 4294967295
r10 0xfffff8015bfff1f0 -8790254554640
r11 0x0 0
r12 0xffffffff 4294967295
...etc...
e.g., setting data breakpoints
(gdb) awatch *0xfffff804683190e0
Hardware access (read/write) watchpoint 1: *0xfffff804683190e0
e.g., single stepping
0xfffff8047a309686 in ?? ()
(gdb) si
0xfffff8047a309689 in ?? ()
You may find this blog post
useful, as it includes a table of common gdb commands along with their WinDbg
counterparts.
Connecting via WinDbg
WinDbg doesn't understand the GDB Remote Serial Protocol directly, but thankfully, some smart folks over on the WinDbg team have developed a GDB Remote Serial Protocol <-> WinDbg translation layer!
For more information, see Setting Up QEMU Kernel-Mode Debugging using EXDI
Getting this working with OpenVMM or OpenHCL is as easy as following the guide, except you'll need to enable our debugger instead of running QEMU.
It's easiest to connect through the GUI. The steps are relatively simple: Open Windbgx -> File -> Attach to kernel -> EXDI. On the form, fill out:
- Target Type:
QEMU - Target Architecture:
X64 - Target OS:
Windows - Image Screening heuristic size:
0xFFFE - NT - Gdb server and port:
<server>:<port>e.g.,127.0.0.1:1337(use whatever port you set above)
Known WinDbg Bugs
- Hardware breakpoints are issued with
ba. TheAccess Sizeparameter is incorrectly multiplied by 8 when sent to the stub. Consequently, it must be set to 1. - Unlike GDB, WinDbg doesn't implicitly set software breakpoints via our offered write_addrs implementation.
Supported Features
At the time of writing (8/16/24) the debugger supports the following operations:
- read/write guest memory
- read guest registers *
- start/interrupt execution
- watchpoints
- hardware breakpoints
- single stepping
TODO Features
If you're looking for work, and want to improve the debugging experience for everyone, consider implementing one or more of the following features:
- * reading all guest registers, including fpu, xmm, and various key msrs
- software breakpoints:
- Intercept guest breakpoint exceptions into VTL2
- writing guest registers
- exposing the OpenVMM interactive console via the
MonitorCmdinterface- Custom commands sent using
monitor(gdb) /.exdicmd(WinDbg) - e.g., being able to invoke
x device/to/inspectdirectly from the debugger
- Custom commands sent using
- any other features supported by the
gdbstublibrary
Kernel Debugging (KDNET)
Kernel Debugging is available for Windows guests via KDNET over VMBus.
Enabling and Starting the Debugger
Set up KDNET on the guest and start the debugger as described on
Set up KDNET network kernel debugging manually | Microsoft Learn.
Setting busparams is not necessary.
With OpenVMM and WHP as Host
Set up the VM for UEFI and VMBus depending on your use case and pass the
additional flag --net consomme:
- Without OpenHCL: Pass the
--uefiflags when starting OpenVMM. - With OpenHCL: Ensure "UEFI Boot" and "VTL2 VMBus Support" are active
Known Issues with KDNET on WHP
- KDNET currently only works with the
consommenetworking option in OpenVMM, howeverconsommewill create a new network adapter in the guest every time OpenVMM is restarted. This can be safely ignored.- KDNET will also connect with
--net vmnic:<ethernet switch id>, but hangs immediately after due to a yet undiagnosed bug in vmbusproxy.
- KDNET will also connect with
- Quitting OpenVMM without shutting down the VM first will prevent the same debugger instance from reconnecting to the guest on next boot. Relauch the debugger to reconnect.
- When launching an OpenHCL VM with KDNET,
virt_whp::synicwill report a constant stream offailed to signal synicerrors for several seconds. These don't appear to affect the VM's functionality and can be ignored.
UEFI: mu_msvm
OpenVMM currently uses the mu_msvm UEFI firmware package in order to support
booting and running modern EFI-boot capable operating systems.
In the future, it would be useful to also support alternative UEFI firmware packages, such as OVMF.
Please reach out of if this is something you may be interested in helping out with!
Two OpenVMM components work in tandem in order to load and run the mu_msvm
UEFI firmware:
-
Pre-boot: the VMM's UEFI firmware loader does 3 things:
- Writes the
mu_msvmUEFI firmware package into guest RAM - Writes VM topology information, and
mu_msvm-specific config data into guest RAM - Initializes register state such that the VM will begin executing from UEFI
- Writes the
-
At runtime: the UEFI code within the Guest interfaces with a bespoke
firmware_uefidevice in order to implement certain UEFI services, such as NVRam variable support, watchdog timers, logging, etc.
Acquiring a copy of mu_msvm
The cargo xflowey restore-packages script will automatically pull down a
precompiled copy of the mu_msvm UEFI firmware from the microsoft/mu_msvm
GitHub repo.
Alternatively, for those that wish to manually download / build mu_msvm:
follow the instructions over on the microsoft/mu_msvm repo, and ensure the
package is extracted into the .packages/ directory in the same manner as the
cargo xflowey restore-packages script.
Hyper-V BIOS
OpenVMM currently relies on proprietary Hyper-V "PCAT"1 BIOS firmware blobs in order to support booting and running various legacy x86 operating systems.
In the future, it would be great if OpenVMM could support alternative, open-source x86 BIOS firmwares, such as SeaBIOS.
Please reach out of if this is something you may be interested in helping out with!
Two OpenVMM components work in tandem in order to load and run the BIOS:
-
Pre-boot: the VMM's BIOS firmware loader writes the PCAT BIOS into guest RAM, and sets up the initial register state such that the VM will begin executing the firmware.
-
At runtime: the BIOS code inside the VM communicates with a bespoke
firmware_pcatvirtual device, which it uses to fetch information about the VM's current topology, and to implement certain BIOS services (such as boot logging, efficient spin-looping, etc).
Acquiring the Hyper-V BIOS Firmware
Unfortunately, due to licensing restrictions, the OpenVMM project is not able to redistribute copies of the proprietary Hyper-V BIOS firmware blob.
That being said - Windows 11 ships copies of the PCAT BIOS firmware in-box under
System32 as either vmfirmwarepcat.dll or vmfirmware.dll. When run on
Windows / WSL2, OpenVMM will automatically scan for these files, and use them if
present.
Fun fact: the term "PCAT" refers to the venerable IBM Personal Computer AT, as a nod to this BIOS's early history as a fairly stock PC/AT compatible BIOS implementation.
NVMe Emulator
Among the devices that OpenVMM emulates, an NVMe controller is one. The OpenVMM NVMe emulator comes in two flavors:
- An NVMe emulator that can be used to serve IO workloads (but pragmatically is only used by OpenVMM for test scenarios today)
- An NVMe emulator used to test OpenHCL (
nvme_test), which allows test authors to inject faults and inspect the state of NVMe devices used by the guest, and
This guide provides a brief overview of the architecture shared by the NVMe emulators.
Doorbells
The doorbell notification system in the NVMe emulator is built around two core structures: DoorbellMemory and DoorbellState. These components work together to coordinate doorbell updates between the guest and the device, following a server-client like model.
 Fig: Basic layout of DoorbellMemory and DoorbellStates.
Fig: Basic layout of DoorbellMemory and DoorbellStates.
Doorbell Memory
DoorbellMemory serves as the central authority for managing doorbell values. It maintains:
- A reference to guest memory, where doorbell registers are mapped.
- A vector of wakers—one per doorbell—to notify tasks when a doorbell is updated.
The emulator creates this struct upon instantiation. All queues receive a reference to the entire list of doorbells. Doorbell writes are handled by the emulator’s PCI interface, which forwards the writes to DoorbellMemory.
Doorbell State
DoorbellState is used by tasks that need to track the value of a specific doorbell. In the NVMe emulator, the SubmissionQueue::tail and CompletionQueue::head are each stored as a DoorbellState. This struct abstracts interactions with DoorbellMemory and synchronization. Tasks can poll the doorbell state. Poll::Ready is returned if the doorbell value was updated.
Waker functionality
To conserve system resources, DoorbellMemory and DoorbellState use wakers to reduce busy-polling when there is no additional work/updates to the doorbell. Instead of repeatedly polling a future value of the corresponding doorbell, when DoorbellState notices no change to the doorbell value, it registers a waker DoorbellMemory and stops polling. When a doorbell write to bar0 is triggered by the guest, DoorbellMemory will write the new value and trigger the corresponding waker, at which point DoorbellState can poll() again and is guaranteed a change to the value (i.e. more work to go do)
 Fig: When a doorbell write comes in and there is a waiting queue, the waker is triggered by DoorbellMemory if there is a registered waker.
Fig: When a doorbell write comes in and there is a waiting queue, the waker is triggered by DoorbellMemory if there is a registered waker.
Architecture
This chapter discusses the architecture of various key parts of the OpenVMM codebase.
OpenVMM Architecture
This page is under construction
OpenHCL Architecture
Prerequisites:
Overview
OpenHCL is a paravisor execution environment that runs within the guest partition of a virtual machine. It provides virtualization services to the guest OS from within the guest partition itself, rather than from the host as is traditionally done.
The following diagram offers a brief, high-level overview of the OpenHCL Architecture.

Virtual Trust Levels (VTLs)
OpenHCL relies on Virtual Trust Levels (VTLs) to establish a security boundary between itself and the guest OS.
- VTL2: OpenHCL runs here1. It has higher privileges and is isolated from VTL0.
- VTL0 (and sometimes VTL1): The Guest OS (e.g., Windows, Linux) runs here. It cannot access VTL2 memory or resources.
This isolation is enforced by the system configured by the underlying virtual machine monitor (Hyper-V) and can be backed by:
Scenarios
OpenHCL enables several key scenarios by providing a trusted execution environment within the VM:
Azure Boost
OpenHCL acts as a compatibility layer for Azure Boost. It translates legacy synthetic device interfaces (like VMBus networking and storage) used by the guest OS into the hardware-accelerated interfaces (proprietary Microsoft Azure Network Adapter (MANA) and NVMe) provided by the Azure Boost infrastructure. This allows unmodified guests to take advantage of next-generation hardware.
The following diagram shows a high level overview of how synthetic networking is supported in OpenHCL over Microsoft Azure Network Adapter (MANA)

The following diagram shows a high level overview of how accelerated networking is supported in OpenHCL over MANA

Confidential Computing
In Confidential VMs (CVMs), the host is not trusted. OpenHCL runs inside the encrypted VM context (VTL2) and provides necessary services (like device emulation and TPM) that the untrusted host cannot securely provide. Security-sensitive devices, such as the virtual TPM, can be further isolated by running them in separate worker processes within VTL2 for defense-in-depth protection.
Trusted Launch
OpenHCL hosts a virtual TPM (vTPM) and enforces Secure Boot policies, ensuring the integrity of the guest boot process.
Architecture Components
OpenHCL is built on top of a specialized Linux kernel and consists of several userspace processes that work together to provide these services.
For more details on the internal components and boot process, see:
Why not VTL1? Windows already uses VTL1 in order to host the Secure Kernel.
OpenHCL Processes and Components
This document describes the major software components and processes that make up the OpenHCL paravisor environment.
Boot Shim (openhcl_boot)
The boot shim is the first code that executes in VTL2. It is responsible for early hardware initialization and preparing the environment for the Linux kernel.
Source code: openhcl/openhcl_boot | Docs: openhcl_boot rustdoc
Key Responsibilities:
- Hardware Initialization: Sets up CPU state, enables MMU, and configures initial page tables.
- Configuration Parsing: Receives boot parameters from the host that were generated at IGVM build time. In the case of isolated VMs,
openhcl_bootwill also filter this host-provided configuration to remove elements that can weaken the isolated VM guarantees (such as exposing debugging interfaces). - Device Tree Construction: Builds a device tree describing the hardware configuration (CPU topology, memory regions, devices).
- Sidecar Initialization: Sets up control structures for the Sidecar kernel (x86_64 only).
- Kernel Handoff: Transfers control to the Linux kernel.
Linux Kernel
OpenHCL runs on top of a minimal, specialized Linux kernel. This kernel provides core operating system services such as memory management, scheduling, and device drivers.
Key Responsibilities:
- Hardware Abstraction: Manages CPU and memory resources.
- Device Drivers: Provides drivers for paravisor-specific hardware and standard devices.
- Filesystem: Mounts the initial ramdisk (initrd) as the root filesystem.
- Process Management: Launches the initial userspace process (
underhill_init).
Sidecar Kernel (x86_64)
On x86_64 systems, OpenHCL includes a "sidecar" kernel — a lightweight, bare-metal kernel that runs on a subset of CPUs to improve boot performance and reduce resource usage.
For more details, see the Sidecar Architecture page.
Source code: openhcl/sidecar | Docs: sidecar rustdoc
Key Responsibilities:
- Fast Boot: Allows secondary CPUs (APs) to boot quickly without initializing the full Linux kernel.
- Dispatch Loop: Runs a minimal loop waiting for commands from the host or the main kernel.
- On-Demand Conversion: Can be converted to a full Linux CPU when required.
Init Process (underhill_init)
underhill_init is the first userspace process (PID 1) started by the Linux kernel. It acts as the system service manager for the paravisor environment.
Source code: openhcl/underhill_init | Docs: underhill_init rustdoc
Key Responsibilities:
- System Setup: Mounts necessary filesystems (e.g.,
/proc,/sys,/dev). - Environment Preparation: Sets up the execution environment for the paravisor.
- Process Launch:
execs the main paravisor process (openvmm_hcl).
Paravisor (openvmm_hcl)
openvmm_hcl is the central management process of the OpenHCL paravisor. It runs in userspace and orchestrates the virtualization services.
Source code: openhcl/openvmm_hcl | Docs: openvmm_hcl rustdoc
Key Responsibilities:
- Policy & Management: Manages the lifecycle of the VM and enforces security policies.
- Host Communication: Interfaces with the host VMM to receive commands and report status.
- Servicing: Orchestrates save and restore operations (VTL2 servicing).
- Worker Management: Spawns and manages the VM worker process.
VM Worker (underhill_vm)
The VM worker process (underhill_vm) is responsible for the high-performance data path of the virtual machine. It is spawned by openvmm_hcl.
Source code: openhcl/underhill_core | Docs: underhill_core rustdoc
Key Responsibilities:
- VP Loop: Runs the virtual processor loop, handling VM exits.
- Device Emulation: Coordinates device emulation for the guest VM. Some devices run in-process while others run in separate device worker processes for isolation.
- I/O Processing: Handles high-speed I/O operations.
Diagnostics Server (diag_server)
The diagnostics server provides an interface for debugging and monitoring the OpenHCL environment.
Source code: openhcl/diag_server | Docs: diag_server rustdoc
Key Responsibilities:
- External Interface: Listens on a VSOCK port for diagnostic connections.
- Command Handling: Processes diagnostic commands and queries.
- Log Retrieval: Provides access to system logs.
Profiler Worker (profiler_worker)
The profiler worker is an on-demand process used for performance analysis (only works if an Microsoft internal-only binary is located at a known location).
Source code: openhcl/profiler_worker | Docs: profiler_worker rustdoc
Key Responsibilities:
- Performance Data Collection: Collects profiling data (e.g., CPU usage, traces) when requested.
- Isolation: Runs in a separate process to minimize impact on the main workload.
Device Worker Processes
OpenHCL supports running chipset device emulators in separate, isolated processes using the chipset_device_worker framework. This provides security isolation and fault tolerance by sandboxing device emulation logic.
Source code: workers/chipset_device_worker | Docs: chipset_device_worker rustdoc
Key Responsibilities:
- Device Isolation: Runs specific device emulators in separate processes to isolate them from the main VM worker.
- I/O Proxying: Forwards device I/O operations (MMIO, PIO, PCI config space) between the VM worker and the device worker.
- Memory Access: Provides proxied access to guest memory for devices that need to read/write VM memory.
- State Management: Handles device save/restore operations across process boundaries.
Current Use Cases:
- TPM Emulation: The virtual TPM (vTPM) runs in a separate device worker process for enhanced security isolation, protecting sensitive cryptographic operations and state from other components.
This architecture can be extended to isolate other chipset devices as needed for security or reliability requirements.
OpenHCL Boot Flow
This document describes the sequence of events that occur when OpenHCL boots, from the initial loading of the IGVM image to the fully running paravisor environment.
sequenceDiagram
autonumber
participant Host as Host VMM
box "VTL2 (OpenHCL)" #f9f9f9
participant Shim as Boot Shim<br/>(openhcl_boot)
participant Sidecar as Sidecar Kernel
participant Kernel as Linux Kernel
participant Init as Init<br/>(underhill_init)
participant HCL as Paravisor<br/>(openvmm_hcl)
participant Worker as VM Worker<br/>(underhill_vm)
participant DeviceWorker as Device Workers<br/>(e.g., TPM)
end
Host->>Shim: 1. Load IGVM & Transfer Control
activate Shim
note over Shim: 2. Boot Shim Execution<br/>Hardware Init, Config Parse, Device Tree
par CPU Split
Shim->>Sidecar: APs Jump to Sidecar
activate Sidecar
note over Sidecar: Enter Dispatch Loop
Shim->>Kernel: BSP Jumps to Kernel Entry
deactivate Shim
activate Kernel
end
note over Kernel: 3. Linux Kernel Boot<br/>Init Subsystems, Load Drivers, Mount initrd
Kernel->>Init: Spawn PID 1
deactivate Kernel
activate Init
note over Init: 4. Userspace Initialization<br/>Mount /proc, /sys, /dev
Init->>HCL: Exec openvmm_hcl
deactivate Init
activate HCL
note over HCL: 5. Paravisor Startup<br/>Read Device Tree, Init Services
HCL->>Worker: Spawn Worker
activate Worker
Worker->>DeviceWorker: Spawn Device Workers (as needed)
activate DeviceWorker
par 6. VM Execution
note over HCL: Manage Policy & Host Comm
note over Worker: Run VTL0 VP Loop,<br/>Proxy Device I/O
note over DeviceWorker: Emulate Isolated Devices
note over Sidecar: Wait for Commands / Hotplug
end
1. IGVM Loading
The boot process begins when the host VMM loads the OpenHCL IGVM image into VTL2 memory. The IGVM image contains the initial code and data required to start the paravisor, including the boot shim, kernel, and initial ramdisk. The host places sections of the IGVM image at headers described by the IGVM format, which includes runtime dynamic data such as the device tree and other configuration values.
2. Boot Shim Execution (openhcl_boot)
The host transfers control to the entry point of the Boot Shim.
- Hardware Init: The shim initializes the CPU state and memory management unit (MMU).
- Config Parsing: It parses configuration from multiple sources:
- Contents of the IGVM image, including:
- Measured parameters Fixed parameters encoded into the measured section of the IGVM image, loaded by the host.
- Command Line: It parses the kernel command line, which can be supplied via IGVM or the host device tree.
- Host Device Tree: A device tree provided by the host containing topology and resource information.
- Contents of the IGVM image, including:
- New Device Tree: It constructs a Device Tree that describes the hardware topology (CPUs, memory) to the Linux kernel.
- Sidecar Setup (x86_64): The shim determines which CPUs will run Linux (typically just the Bootstrap Processor (BSP)) and which will run the Sidecar (APs). It sets up control structures and directs Sidecar CPUs to the Sidecar entry point.
- Sidecar Entry: "Sidecar CPUs" jump directly to the Sidecar kernel entry point instead of the Linux kernel.
- Dispatch Loop: These CPUs enter a lightweight dispatch loop, waiting for commands.
- Kernel Handoff: Finally, the BSP (and any Linux APs) jumps to the Linux kernel entry point, passing the Device Tree and command line arguments.
3. Linux Kernel Boot
The Linux Kernel takes over on the BSP and initializes the operating system environment. Sidecar CPUs remain in their dispatch loop until needed (e.g., hot-plugged for Linux tasks).
- Kernel Init: The kernel initializes its subsystems (memory, scheduler, etc.).
- Driver Init: It loads drivers for the paravisor hardware and standard devices.
- Root FS: It mounts the initial ramdisk (initrd) as the root filesystem.
- User Space: It spawns the first userspace process,
underhill_init(PID 1).
4. Userspace Initialization (underhill_init)
underhill_init prepares the userspace environment.
- Filesystems: It mounts essential pseudo-filesystems like
/proc,/sys, and/dev. - Environment: It sets up environment variables and system limits.
- Exec: It replaces itself with the main paravisor process,
/bin/openvmm_hcl.
5. Paravisor Startup (openvmm_hcl)
The Paravisor process (openvmm_hcl) starts and initializes the virtualization services.
- Config Discovery: It reads the system topology and configuration from
/proc/device-treeand other kernel interfaces. - Service Init: It initializes internal services, such as the VTL0 management logic and host communication channels.
- Worker Spawn: It spawns the VM Worker process (
underhill_vm) to handle the high-performance VM partition loop.
6. VM Execution
At this point, the OpenHCL environment is fully established.
The underhill_vm process runs the VTL0 guest, handling exits and coordinating device emulation. During VM initialization, security-sensitive devices requiring isolation (such as the virtual TPM) are spawned as dedicated device worker processes that run the emulation logic in separate, sandboxed processes. The VM worker proxies I/O operations and guest memory accesses between the guest and these isolated device emulators.
Meanwhile, openvmm_hcl manages the overall policy and communicates with the host.
Sidecar Kernel (x86_64)
On x86_64, OpenHCL includes a sidecar kernel - a minimal, lightweight kernel that runs alongside the main Linux kernel.
Source code: openhcl/sidecar | Docs: sidecar rustdoc
Why Sidecar?
Booting a full Linux kernel on every CPU is expensive, especially for Virtual Machines with large CPU counts (e.g., hundreds of vCPUs). Initializing the kernel data structures, per-CPU memory, and scheduling threads for every core takes significant time and memory.
The sidecar kernel solves this by:
- Parallelism: It allows many VPs to be brought up concurrently without contention on Linux kernel locks.
- On-Demand Scaling: CPUs can be dynamically converted from running in the sidecar to full Linux on demand (this is a one-way transition).
How It Works
During the boot process, the Boot Shim determines which CPUs will run the main Linux kernel and which will run the sidecar kernel.
- Linux CPUs: A small subset of CPUs (often just one or one per NUMA node) boot into the full Linux kernel to handle system services, device drivers, and the control plane.
- Sidecar CPUs: The remaining CPUs boot into the lightweight sidecar kernel.
The boot shim passes this assignment to the Linux kernel via command-line parameters and to the sidecar kernel via configuration pages in memory.
The Sidecar Loop
The sidecar kernel executes a simple dispatch loop on each CPU:
- Halt: The CPU halts (mwait/hlt) until it receives an interrupt or a command.
- Command Processing: It handles simple commands from the host VMM, such as "Run VP" (execute the guest VTL0 code).
- Conversion: If the CPU is needed for a task that requires full Linux capabilities (e.g., handling a complex I/O interrupt or running a userspace process), it can be commanded to "hot-plug" itself into the running Linux kernel.
Communication
Communication between the Linux kernel, the host, and the sidecar CPUs occurs through:
- Control Page: Shared memory for kernel-to-sidecar communication (one per NUMA node).
- Command Pages: Per-CPU pages for VMM-to-sidecar commands.
- IPIs (Inter-Processor Interrupts): Used to wake up sidecar CPUs when work is available.
IGVM Image
The Independent Guest Virtual Machine (IGVM) format describes the initial state of an isolated virtual machine. OpenHCL is delivered as an IGVM image.
Note: For more details on the IGVM specification, see the IGVM repository.
Purpose
The IGVM file serves as the "firmware image" for the OpenHCL paravisor. It allows the host VMM to:
- Load the OpenHCL components into VTL2 memory.
- Place them at specific, required physical addresses in. (Components are loaded in a well-defined order to ensure that measurements are reproducable).
- Pass initial configuration data to the paravisor.
IGVM Image Contents
An OpenHCL IGVM image bundles the following artifacts:
- Boot Shim (
openhcl_boot): The entry point for VTL2 execution. - Linux Kernel: The operating system kernel.
- Sidecar Kernel (x86_64): The lightweight kernel for APs.
- Initial Ramdisk (initrd): The root filesystem containing userspace binaries (
underhill_init,openvmm_hcl, etc.). - Memory Layout: Directives specifying where each component should be loaded in memory.
- Measurements: Information that the underlying platform uses to confirm that the file was loaded correctly and signed by the appropriate authorities.
- Configuration: Boot-time parameters. This includes the data that is known at build time (and measured), and data that is not known until the VM is started (e.g. CPU topology, device settings, etc.). See
ParavisorMeasuredVtl0ConfigandParavisorMeasuredVtl2Configfor examples of data known at build time.
Build Process
The IGVM artifact is generated by the OpenHCL build system. See Building OpenHCL for instructions on how to build it.
OpenVMM Rust Crate API Docs
Rust crate API documentation generated by cargo doc is available at the
following URLs:
- Linux x86 - https://openvmm.dev/rustdoc/linux/openvmm
- Windows x86 - https://openvmm.dev/rustdoc/windows/openvmm